# Objects
# IP Objects
FWCloud supports a variety of object types like Addresses, Ranges, Networks, Domain names, Hosts, IPTables marks and Groups. Think in objects like a more convenient way to refer an element of a firewall rule or a VPN configuration.
For example instead of using '224.0.0.5' you can use 'OSFP (all routers)' that is more readable, or you can use 'First flour switches' instead of including in your rule all IP addresses of the switches of that particular flour.
Every kind of objet has its own block. Check next sections in this help to know which fields has every type of objects.
# Addresses
Represent an IP address in both IPv4 and IPv6. To add new IP addresses, just hover the mouse over IP Address and select New IP address from the context menu.
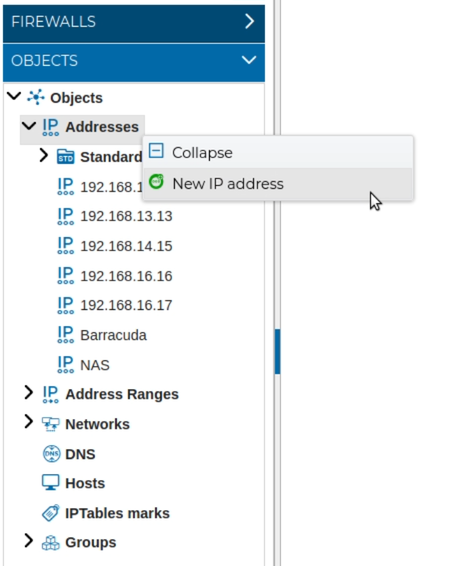
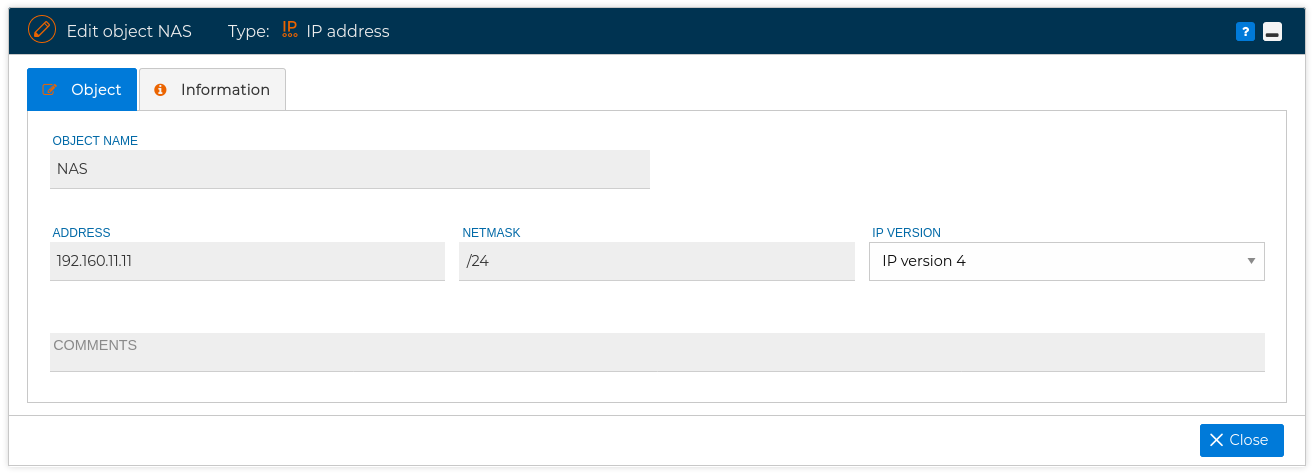
You get a new form, the fields of this objects are: name, address, netmask, IP version and comments.
If you expand IP Address block you see a subsection called Standard. For your convenience the wellknown standard IP addresses has been included inside.
Here you have a list of the IP addresses in the Standard block:
| Name | Address |
|---|---|
| all DVMRP | 224.0.0.4 |
| all-hosts | 224.0.0.1 |
| all-routers | 224.0.0.2 |
| DHCP server, relay agent | 224.0.0.12 |
| EIGRP | 224.0.0.10 |
| HSRP | 224.0.0.102 |
| IGMP | 224.0.0.22 |
| LLMNR | 224.0.0.252 |
| mDNS | 224.0.0.251 |
| OSPF (all routers) | 224.0.0.5 |
| OSPF (designated routers) | 224.0.0.6 |
| OSPFIGP-TE | 224.0.0.24 |
| PIM | 224.0.0.13 |
| RIP | 224.0.0.9 |
| RSVP | 224.0.0.14 |
| Teredo | 224.0.0.253 |
| VRRP | 224.0.0.18 |
# Address Ranges
Allow you to define a range of IP addresses, and give it a name you can use in the policy rules, for instance from 192.168.1.0 to 192.168.4.231.
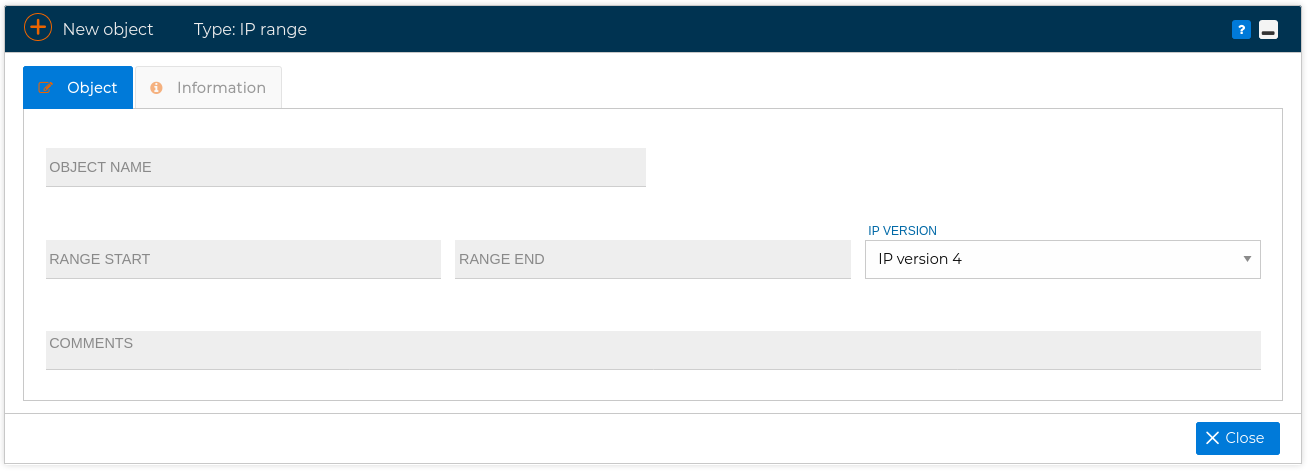
Two Standard address ranges has been included:
| Name | Range start | Range end |
|---|---|---|
| broadcast | 255.255.255.255 | 255.255.255.255 |
| old-broadcast | 0.0.0.0 | 0.0.0.0 |
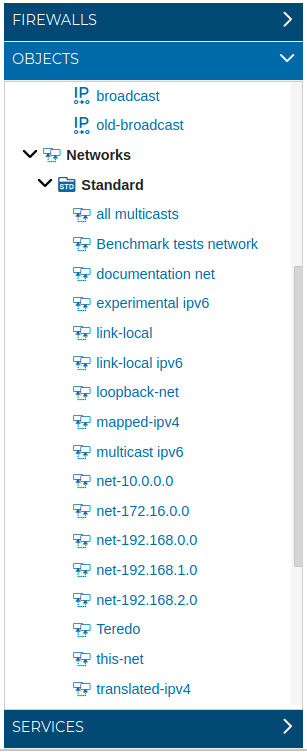
# Networks
You can define a network (Visitor LAN, Control network, etc.) using the IP address and its net mask.
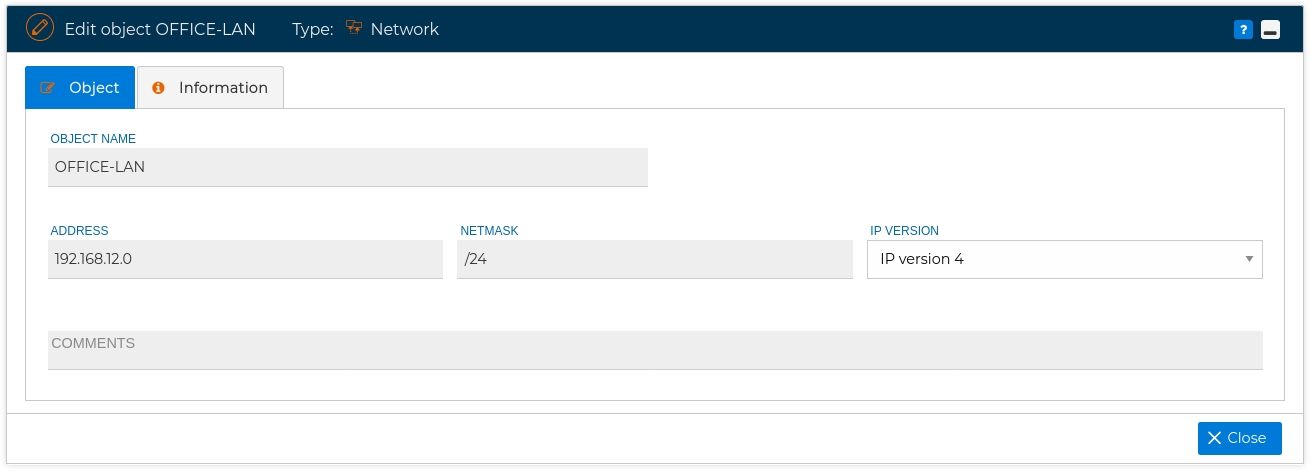
Also this section includes a list with the Standard networks
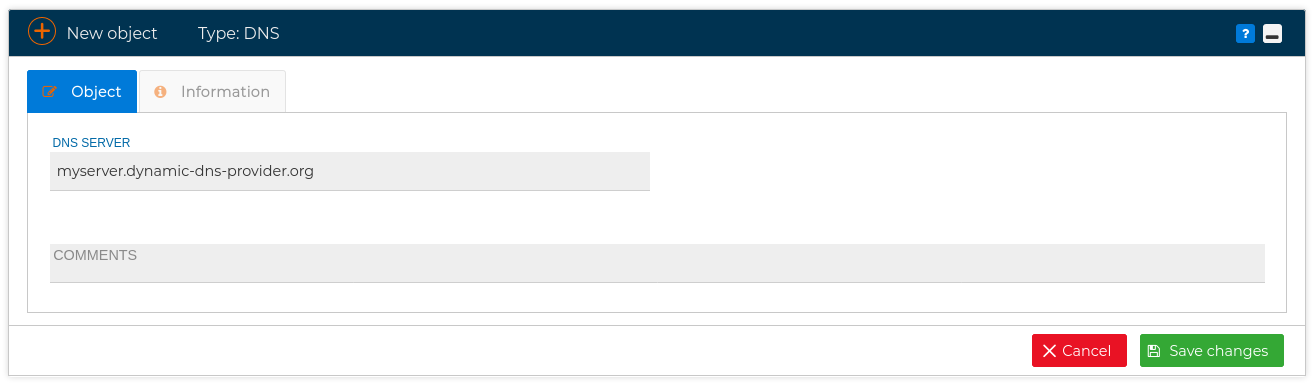
# DNS
If your servers or routers have dynamic IP address you can use the FQDN. This is quite useful when creating the configuration file of a VPN connection. (Visit VPN section )
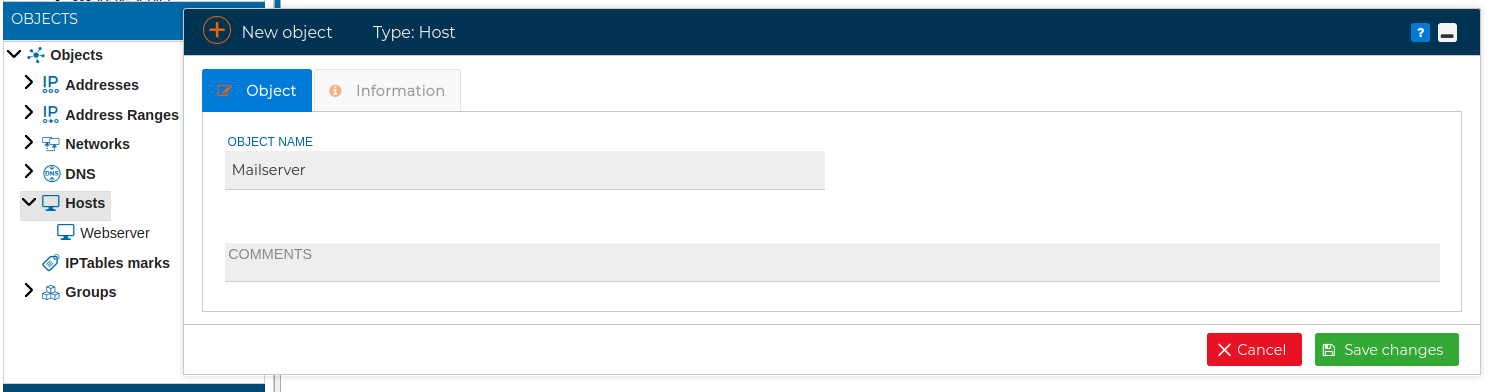
# Hosts
You can define a host by its name and then define its network interfaces and the IP addresses. Then when you include that IP address in a rule it will be more easy to identify which host it belongs to.
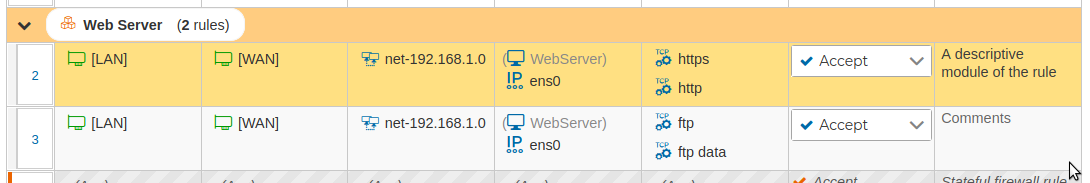
Let's see some policy rules including this new defined host:
# IPTables Marks
You can create marks values to get them associated with specific packets and then do advanced routing or set different queueing strategies. This marks are only valid within the mangle table. In FWCloud-UI marks have a name an code, an integer value that is actually the mark when translated into IPTables syntax.
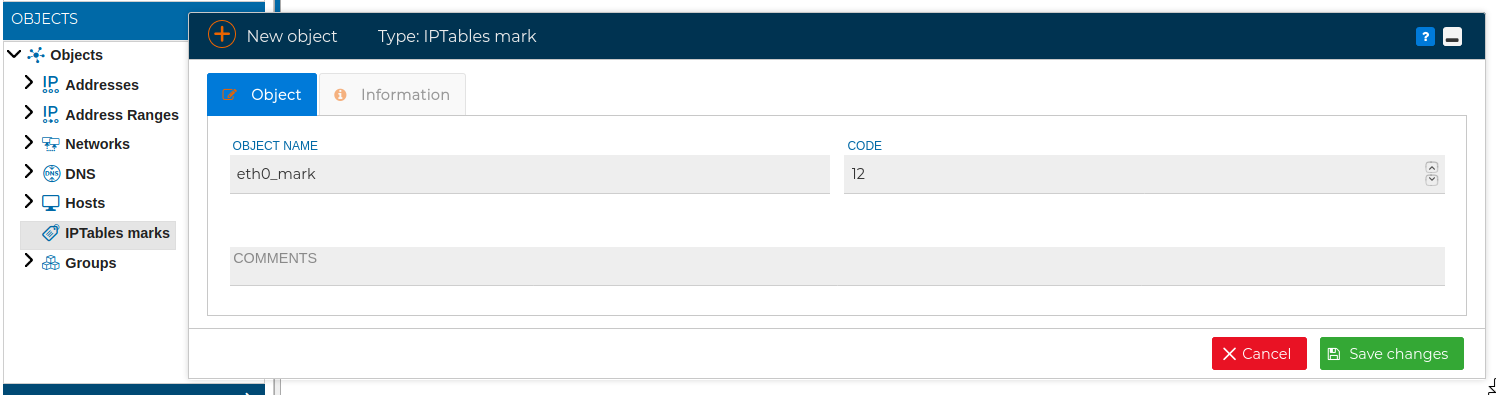
To use these marks drag them from the Objects section and drop them in the Action field of the the policy rules.
# Groups
This objects acts as a container of other objects. This way you can have a group that includes some of your networks, or some IP address of your organization that are related in same way, and use then as a whole. For instance one of the groups already defined is rfc1918-nets that includes all of the IPv4 addresses for private networks. This group is formed from three previously defined network objects.
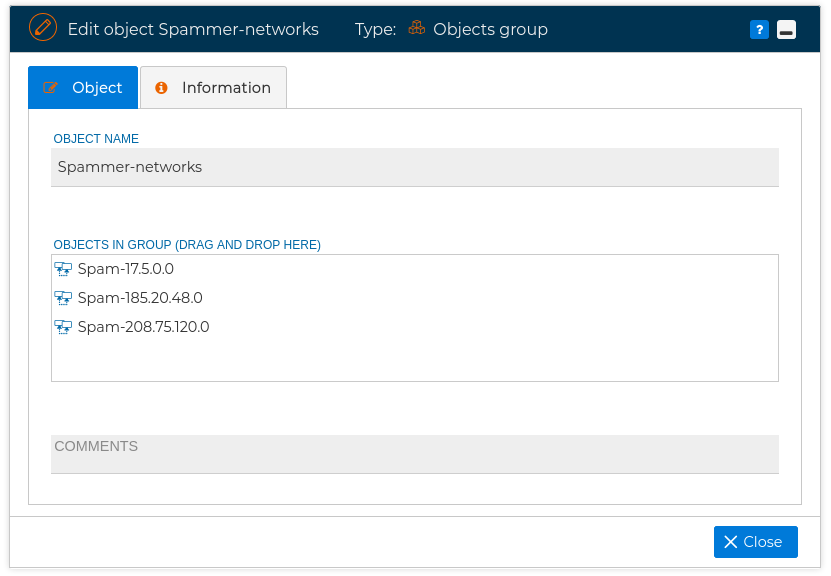
Here you can see the groups already defined in the Standard block:
# Countries
Depending on the type of organization, any traffic coming from or destined to certain countries can be considered at least suspicious.
We can use this information to prevent DOS and DDoS attacks originating from certain countries.
FWCloud-UI has a special type of objects that represent IP addresses geolocated in each of the countries.
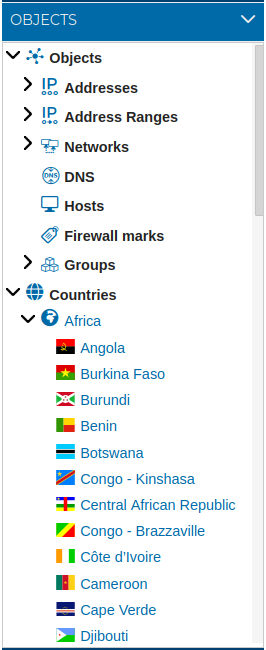
For organizational reasons countries are grouped into the continents they belong to:

We can use the countries in the fields of the security policy table. Graphically, the objects have the flag of the country, which allows a quick reading of the created rule.
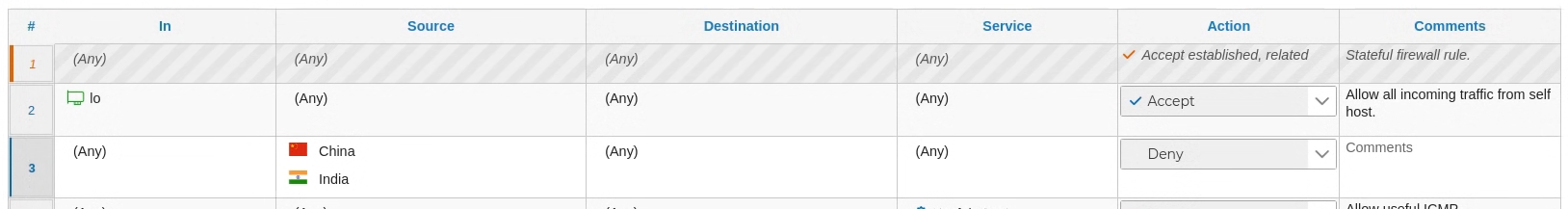
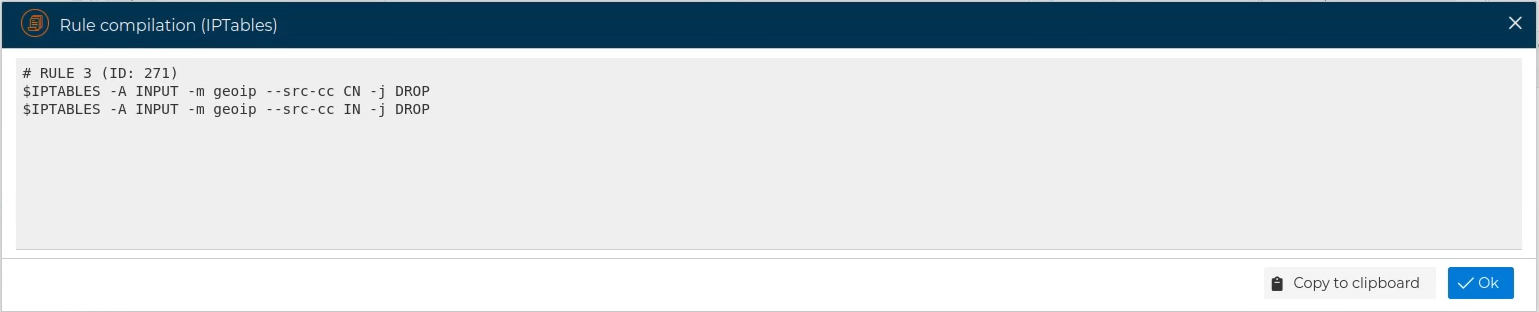
To see the generated code we are going to compile the last rule of the table shown in the previous image
In addition to being able to use each of the countries individually, to simplify certain rules we can use the group object that represents all the countries of a certain continent, dragging the icon of this continent

Watch a video about this type of objects
# Services
In any Policy rule you have to add the services involved, or any, to restrict the scope of the rule. In FWCloud-UI this is done by dropping services from the Services block.
If you expand this block the services are classified into five main groups:IP, ICMP, TCP, UDP and Groups.
All categories include a subsection with the Standard block of services included.
# IP
Here you can add the IP protocol numbers. This is the value you can find in the field "Protocol" in IPv4 or in "Next Header" in IPv6. The numbers defined by IANA has been defined yet inside the Standard folder.
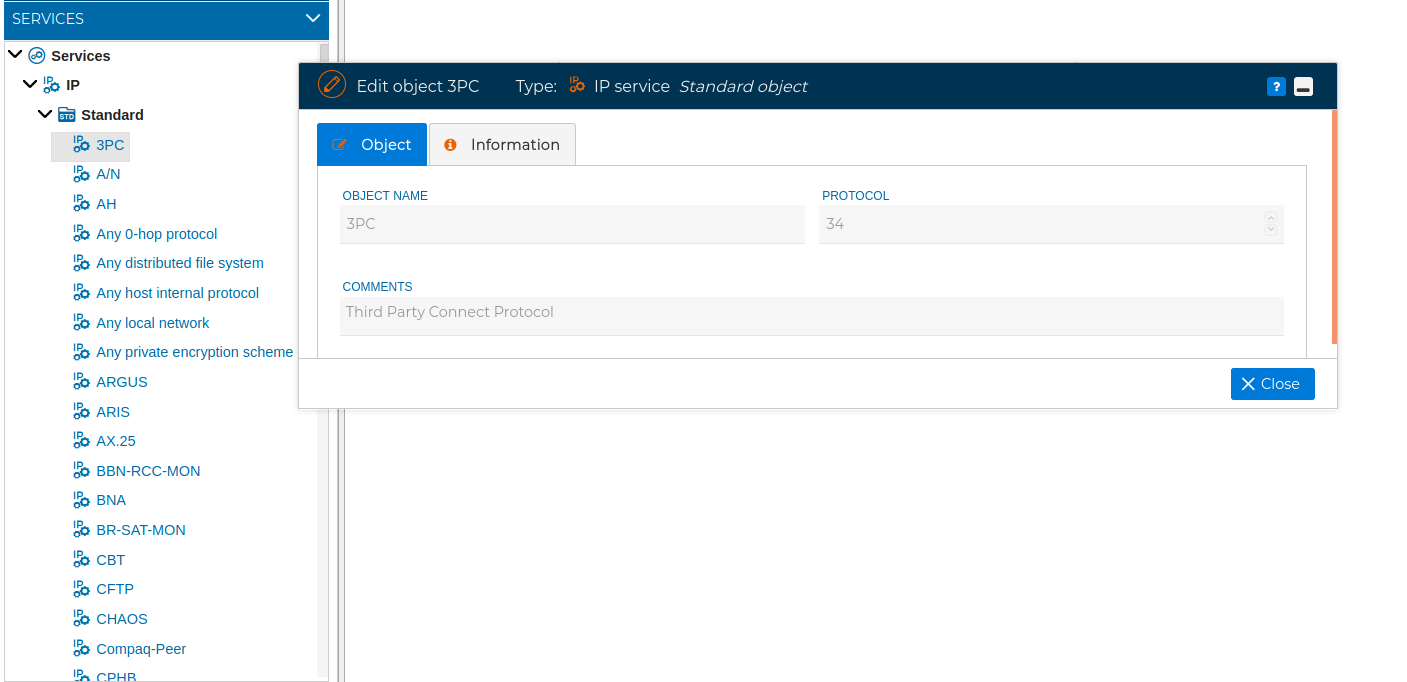
In order to add a new object of IP service type, just right click over IP and select New IP service and fill the form with the name and the protocol number
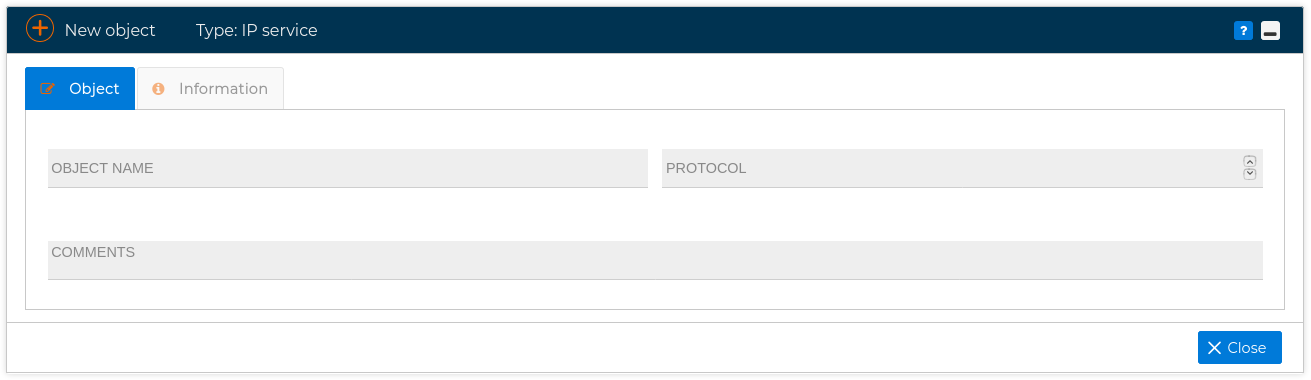
# ICMP
In this section you have the ICMP service objects that make reference to the messages of the Internet Control Messages Protocol. In the Standard folder you have the ICMP messages defined in the RFC documents. To add a new one you need to write the name, its ICMP type and its ICMP code.
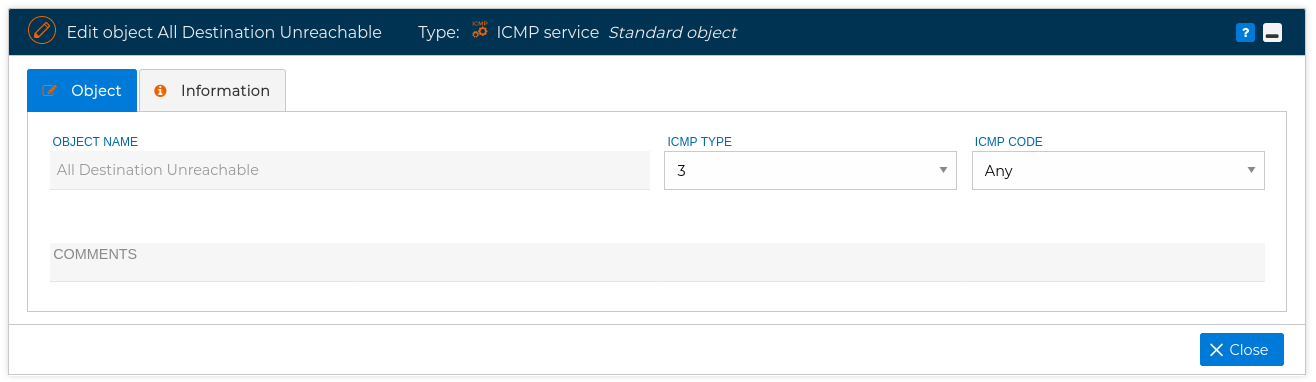
# TCP
This type of objects makes reference to the TCP port numbers designated for used with a certain protocols or applications. In the Standard folder has been included vast list of the well-known and the registered ports.
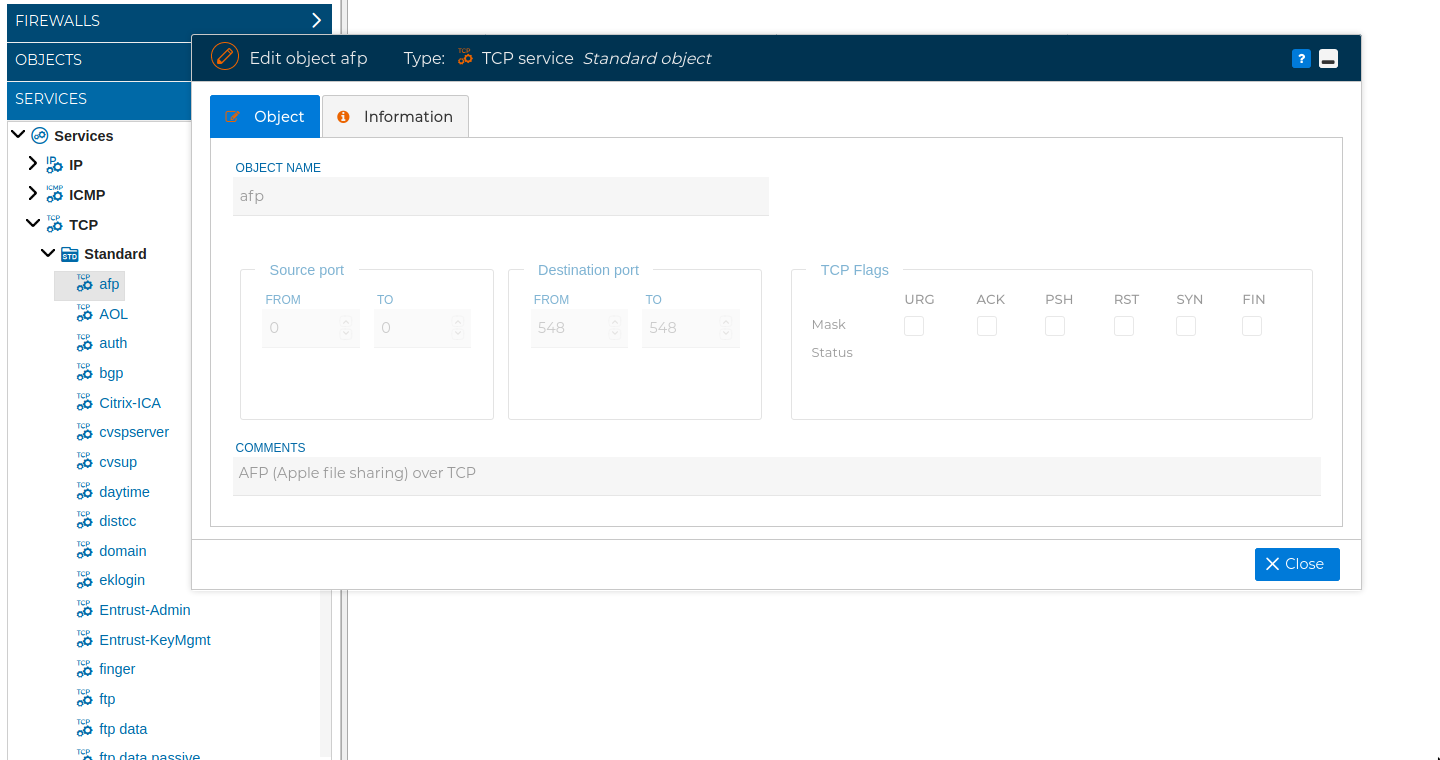
As with the other types of objects you can add more to suit your needs.
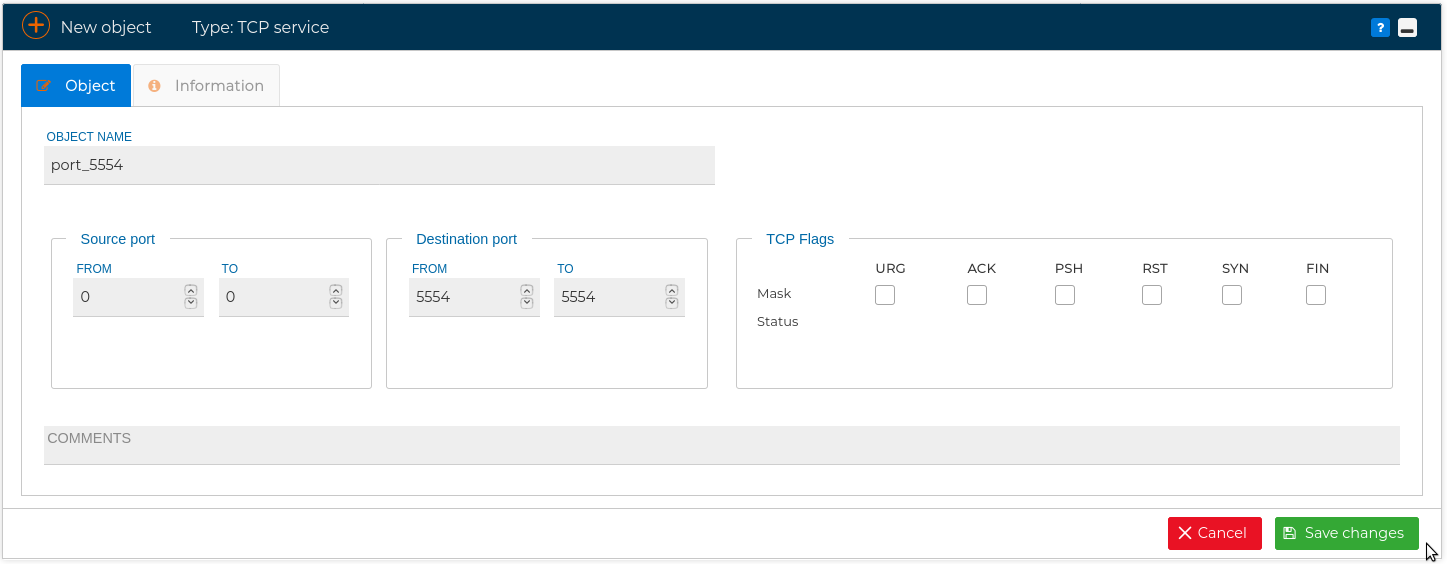
Note that when defining a new TCP service, you can customize the source port and the destination port. Usually only the destination port is used.
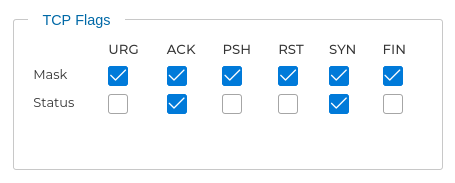
You can also specify the TCP flags. This option accepts two parameters. The first parameter is the mask, which sets the flags to be examined in the packet. The second parameter refers to the flag that must be set in order to match the rule.
For example if you want all the flags to be examined but only ACK and SYN must be active:
# UDP
This type of objects make reference to the UDP port numbers designated for used with a certain protocols or applications. In the Standard folder has been included vast list of the well-known and the registered ports.
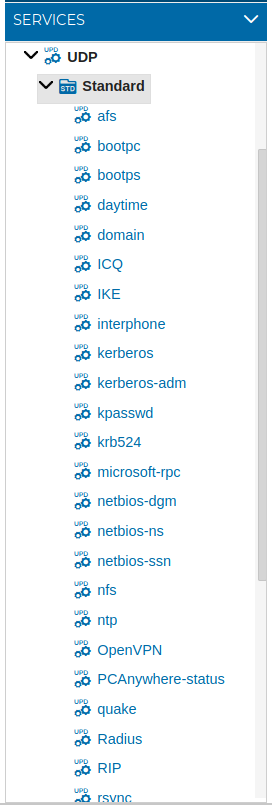
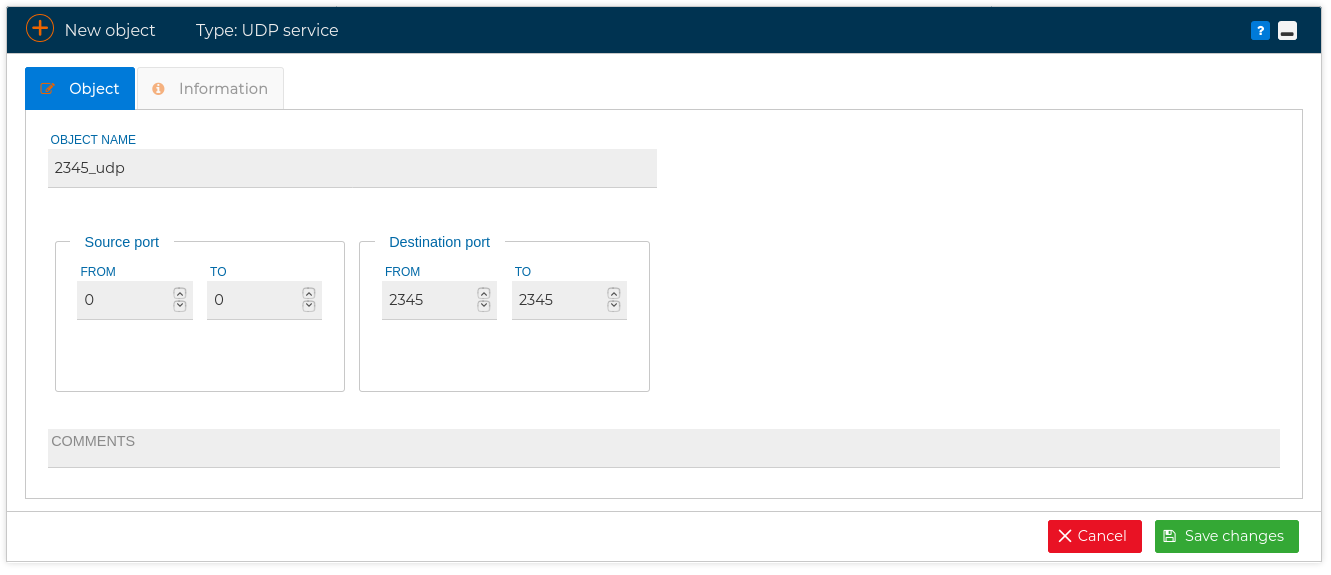
More ports can be added to this list when needed.
# Groups
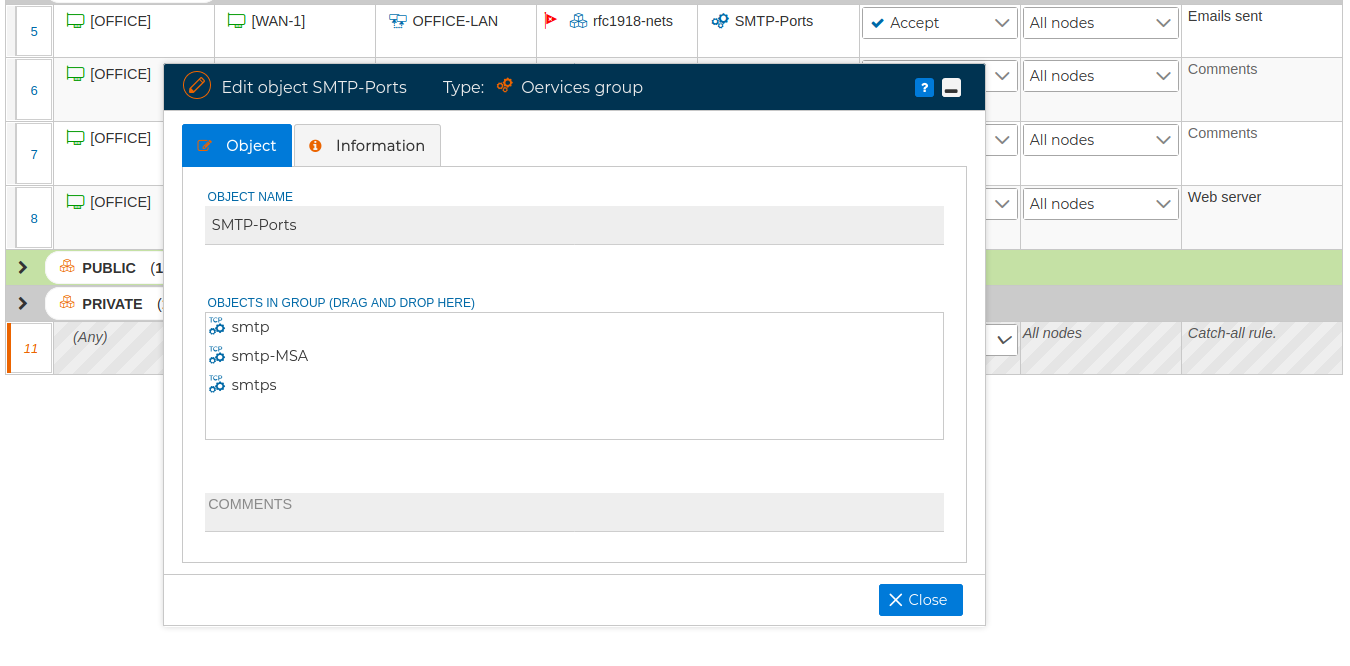
For simplicity and better reading of the policy rules, several services can be grouped together and referenced by a group name. For instance you can create a group called "SMTP-Ports" and include following TCP services in it: smtp (25), smtp-MSA(587) and smtps(465)
FWCloud-UI came with three groups included in the Standard folder, they are called: DHCP, NETBIOS and Useful ICMP. You can use them or as an example for creating your new own groups.
# Searching
In order to quickly find any of the objects you can use the search box.
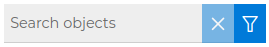
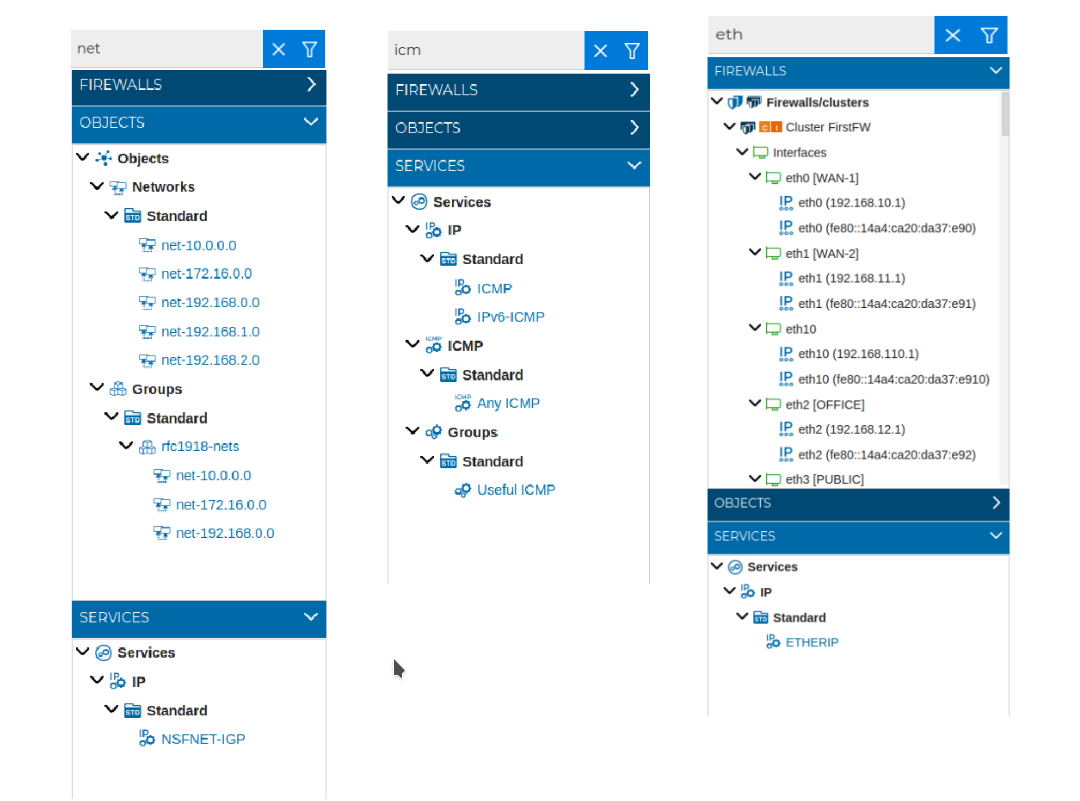
The content displayed in any of the sections: Firewalls, Objects or Services will be filtered by the text entered into the search box as you are typing, limiting the shown results. All folders and groups that have object names that match the searching pattern will be expanded to display them, no matter if they are standard objects or defined by the user.
The default criteria is to match all but this option can be configured. At least one option must be checked, but you can check more than one.
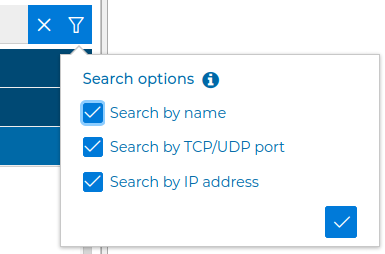
The text pattern can be searched in the names of the objects ("Search by name"), or in their values. When "Search by TCP/UDP port" is selected, the port number of the pattern requires an exact match, because the result includes not only the object that has this port as its value but also all the ranges it is included in. That is, if 8080 is searched, the "TCP high ports" standard object also will also be displayed, among others, since its range goes from 1024 to 65535.
Once you find the object you are looking for you can drag and drop it on any rule of the security policy.
When you clear the search box everything will be expanded showing the full content of the sections.
# Objects operations
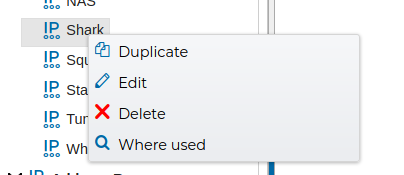
# Duplicate
From the contextual menu of the objects they can be duplicated. This is useful when you are creating objects of the same type that have common properties. For instance several IP addresses that belong to the same network. All of them share the network address and mask. Instead of creating a new object for each you can create only the first one, duplicate it and then modify only the host part of the address.
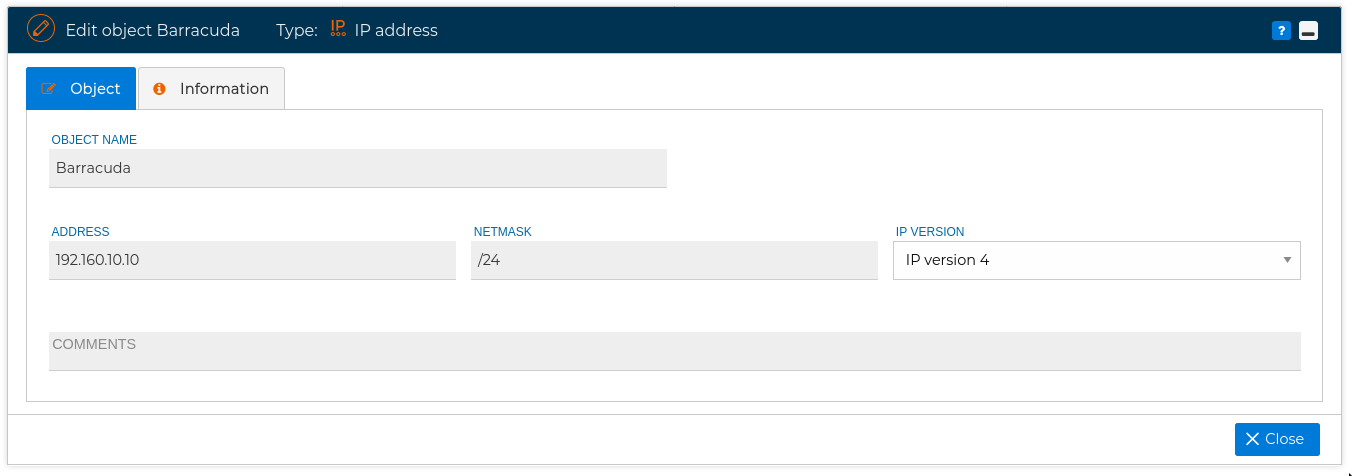
# Edit
In order to modify an object you can double click on its name or select "Edit" from the contextual menu. You will be presented a form with all the object properties. You can edit the values of these properties to suit your needs.
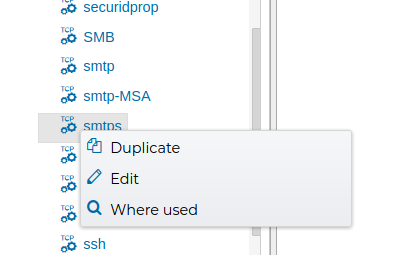
# Where used
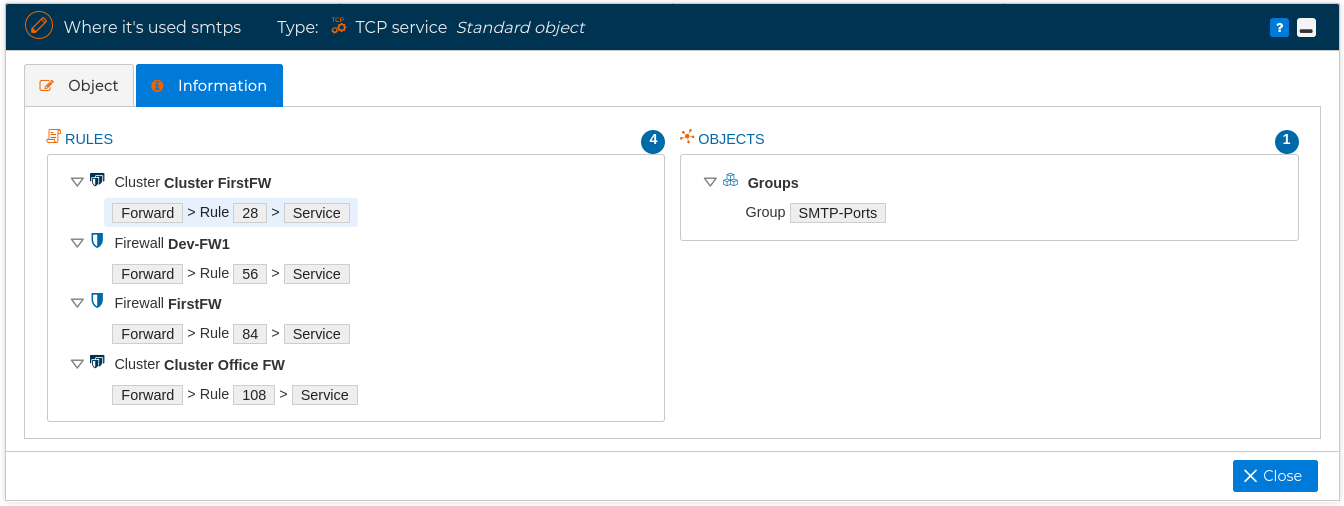
Another feature very useful is that you can right click on any object of FWCloud-UI and select Where used ffrom the contextual menu
and a form pops up indicating all the places where this object is used. For example, the following figure show the objects and rules that make use of service object "smtps".
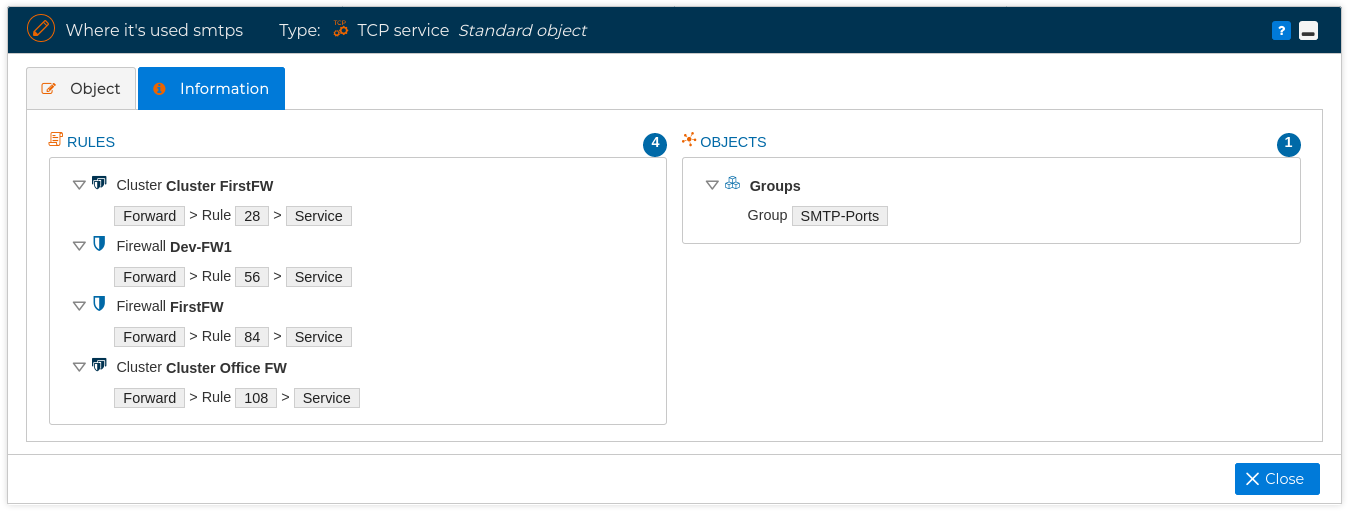
If we double click on any of the objects of the form it will head us to the place where the object is used. For instance, if whe double click on the rule 28 of the cluster named "Cluster FirstFW" we will be presented with the rule of this cluster policy and remaking the field than contains the object with a light blue background.
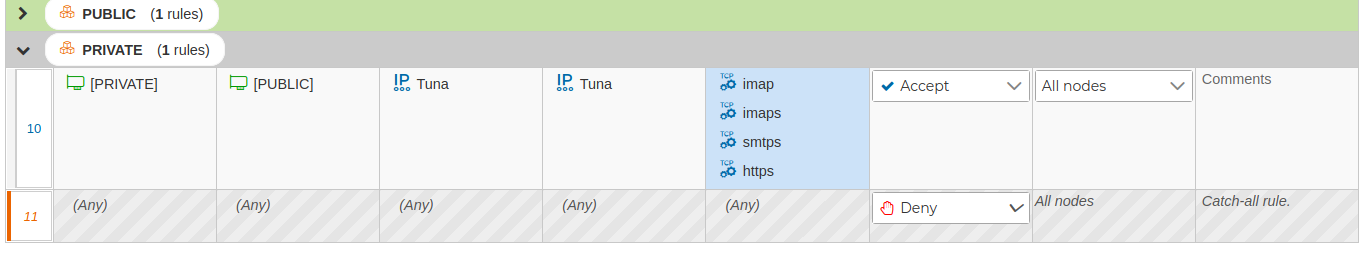
If you want to go the the next rule or group that use the object just click on the ![]() icon and you get back to the "Where used" window. This window will remark the object reviewed in light blue background.
icon and you get back to the "Where used" window. This window will remark the object reviewed in light blue background.
# Delete
For any user created object there is an extra option in the contextual menu to delete de object.
If you try deleting an object that is in use, FWCloud-UI is going to warn you about this and will not allow you to delete the object until the restrictions are removed.
A pop up windows will show where the object is being used.
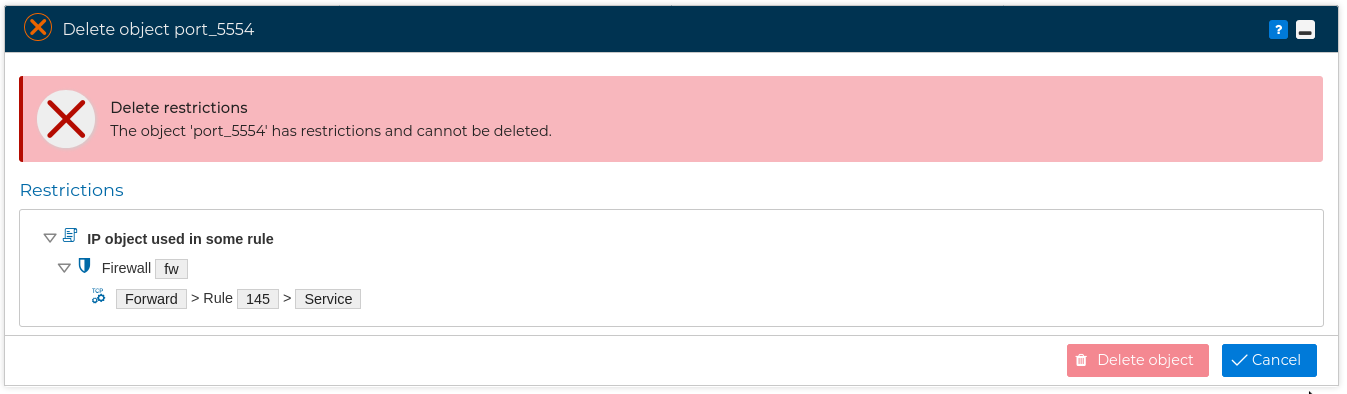
If you double click on any of the showed rules FWCloud-UI will redirect you to that rule remarking the object in light blue background.
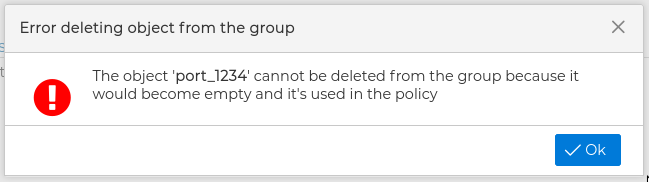
There is another important restriction. If an object belongs to a group that only has this object and this group is used in a policy rule, then the object can not be deleted. This is because allowing to do that would lead to an incorrect policy. Let's see this with an example:
Imagine a public service group that has only the user-created service, TCP-1234, and that group is used in a rule that allows services in that group to access a server from the Internet.

If FWCloud-UI allowed the deletion of the TCP-1234 service (which is the only element of the group used in the rule), we would leave a rule that would allow access to any service (the group is empty) of that server. When compiled that rule would be: "$IPTABLES -A FORWARD -i eth0 -o eth1 -d 192.168.0.1 -m conntrack --ctstate NEW -j ACCEPT" , that probably is not our intention. So FWCloud-UI throws an error:
# Information Bubbles
When we mouse over objects and wait a couple of seconds, an info bubble pops up. These bubbles are quite useful when revising policy rules or creating new ones, since we don't need to look up the object to know its properties.
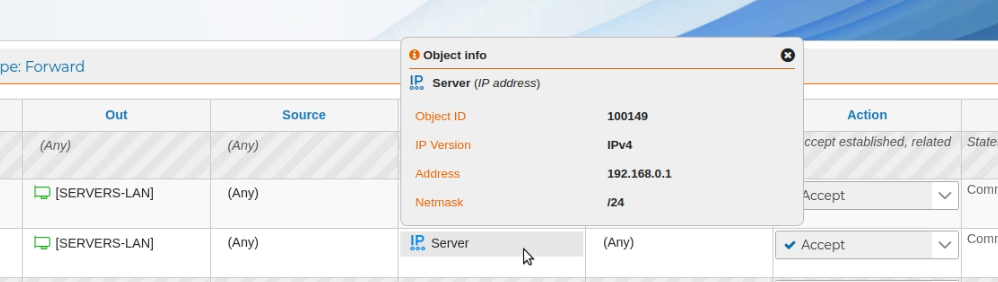
In the above screenshot we can check the IP address associated to "Server" is "192.168.0.1" and it has "/24" as netmask.
This way, and without leaving the rule, we can make sure that the object is exactly the one we want to use in that place, or see which object or objects, in the event that it is a group, is referring to the revised rule.
Sometimes for whatever reason we are not interested in this information, it can even annoy us since it hides part of the screen with the rules we are studying. We can always close it by clicking on the cross in the upper right side of the globe, but it can be even more convenient to tell FWCloud-UI not to show us this information. We can control this functionality with the ![]() icon at the top of the interface.
icon at the top of the interface.
![]()
This icon changes its color to black ![]() when info bubbles are disabled. Clicking on the icon again, it turns orange
when info bubbles are disabled. Clicking on the icon again, it turns orange ![]() and the functionality is enabled again.
and the functionality is enabled again.
