# VPN
FWCloud has full integration between VPN and secure Policy. From FWCloud-UI you can create and manage your Public Key Infrastructure (PKI).
# CA
In order to be able to issue and revoke certificates you need to have Certificate Authority (CA). It is the trusted entity that gives legitimacy to the relationship of a public key with the identity of a user or a service.
# New CA
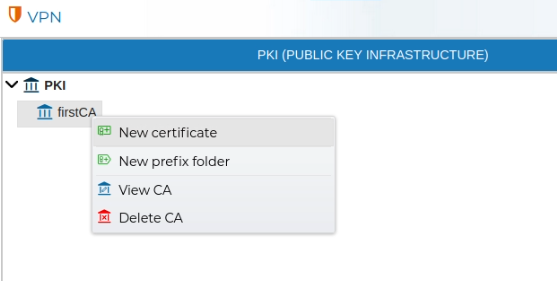
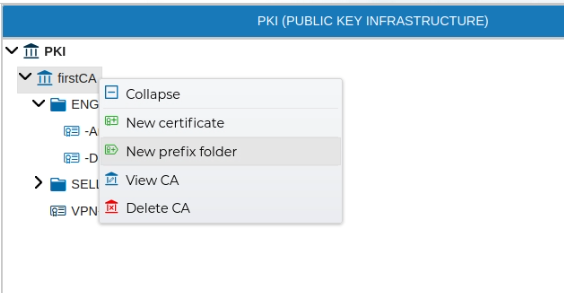
In the PKI area right click on the icon and select New CA
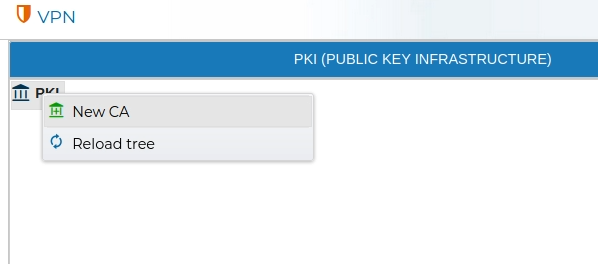
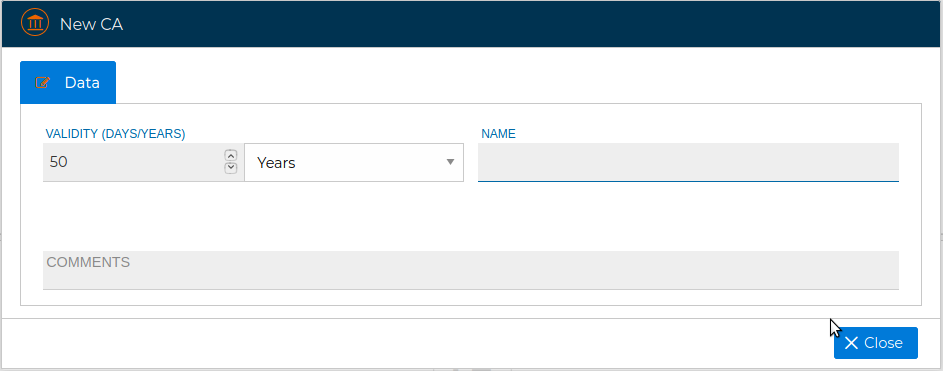
You need to provide a name and the valid period for the new CA.
The process of generating a new CA can last a little bit. It is carried out in the background, you can continue working with FCloud-UI.

# View
The settings of a CA can be reviewed by double clicking over the CA name or right click and select View CA.
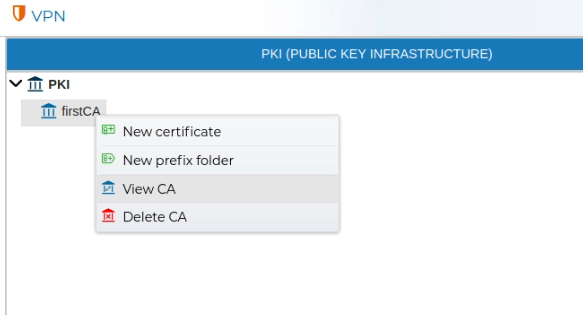
The information displayed cannot be modified.
# Delete
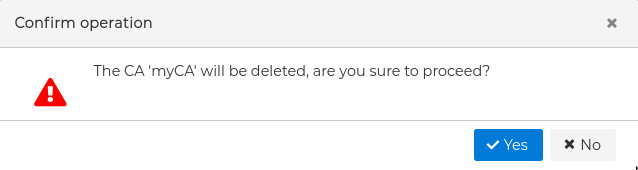
In order to remove a CA, right click over the CA name and select Delete CA.
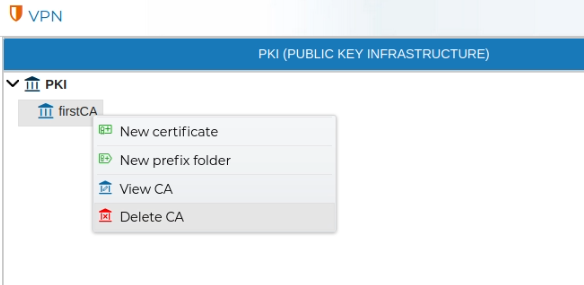
If you try to delete a CA that has issued certificates than has not been removed yet you will receive a warning and the deletion will not be carried out.
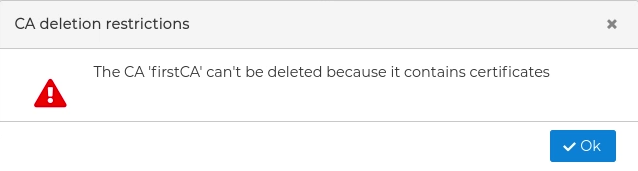
In case the deletion is possible first you will be asked for confirmation.
# Certificates
One of the objectives of the PKI is configuring VPN connections. You will need a certificate for the VPN server and a certificate for any of the clients that will connect to that server.
# New Server Certificate
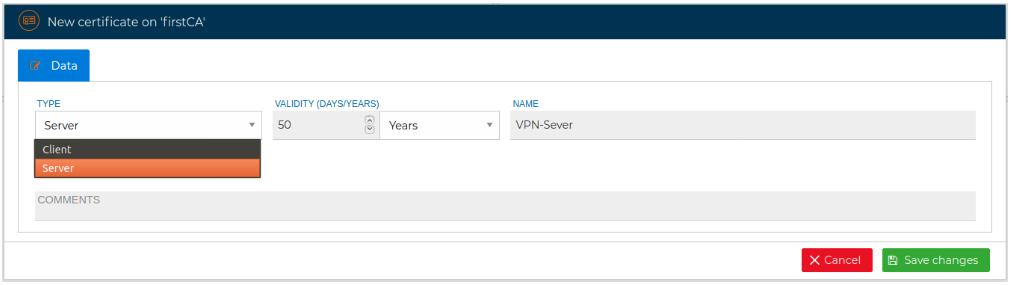
New certificates can be issued from the CA.
For a server certificate select Server as the type of the certificate in the drop down selection box.
# New Client Certificate
The process for issuing a client certificate is almost the same as for a server certificate. From the CA select New certificate and select Client as the type of the certificate in the displayed form.
The form changes proposing a style for the name of the certificate that includes the name of the company, the country, the department, the name to whom the certificate is issued and a number in the event that more than one certificate is issued for the same person.
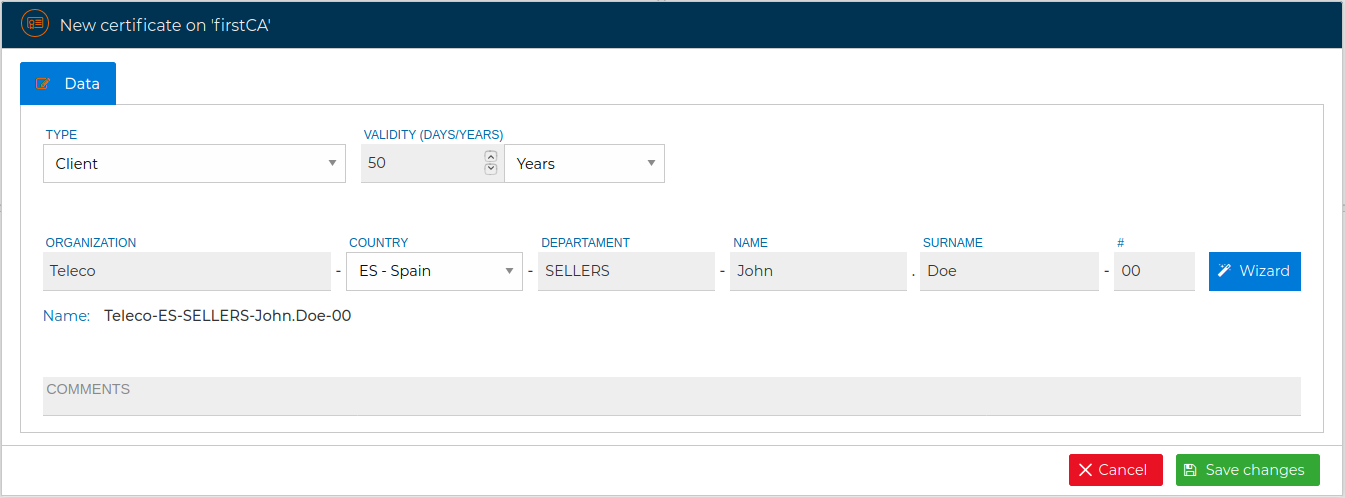
You can follow this nomenclature or hide this wizard by clicking on the "Wizard" button and directly write the name of the certificate.
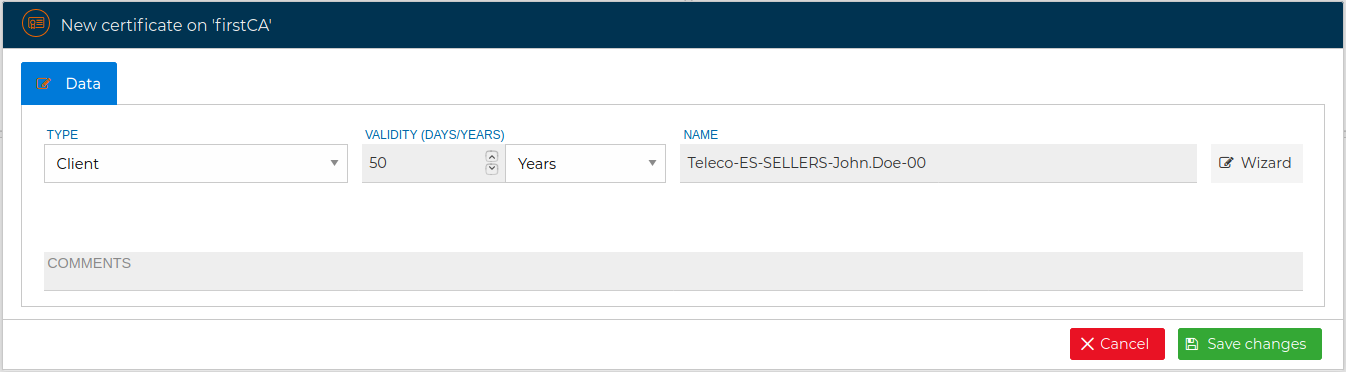
You must fill the name and the validity period and save the changes. If every goes fine you will see a message in the right top corner of FWCloud-UI.
As a good practice, if the certificate is issued for a person, we recommend to include his name in the name of the certicate. Also, consider to append a number at the end of name of the certificate. If the client needs another certificate in the future just increase that number.
# View
Server and client certificates can be reviewed by double clicking over the certificate name or right click and select View certificate.
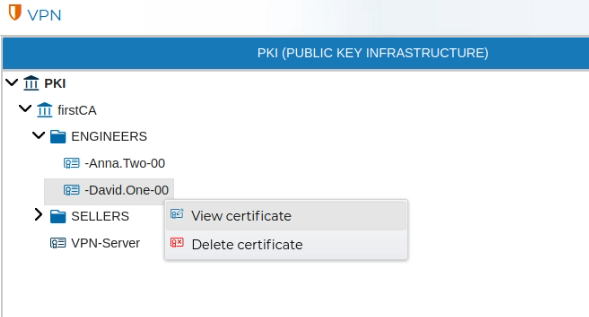
The information displayed cannot be modified.
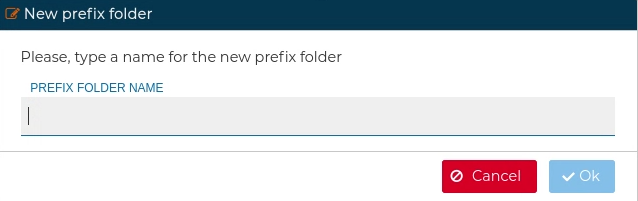
# Prefixes
In order to keep the certificates ordered you can create a folders. This are called Prefix in FWCloud-UI terms. All certificates which their name start with that prefix name will be automatically included inside this folder. The prefixes group the certificates under one name. They can be created in the PKI section.
# Delete
When a certificate is no longer needed, it can be removed. Right click over the certificate name and select Delete certificate.
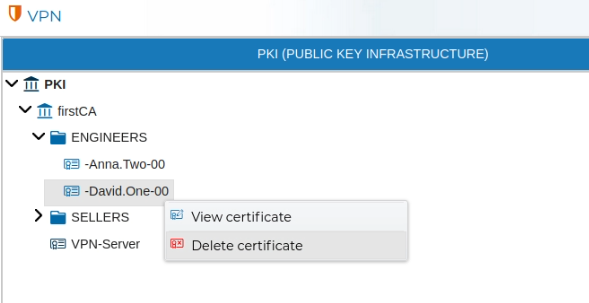
FWCloud-UI does not allow to delete certificates if they are in use. First remove any of the VPN settings that make use of them.
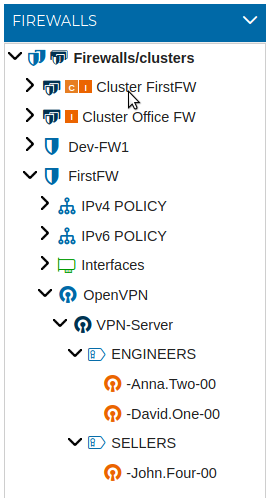
# OpenVPN
# Server Configuration
To use the server certificate drag it and drop it over the name of the firewall that is going to be the VPN server.
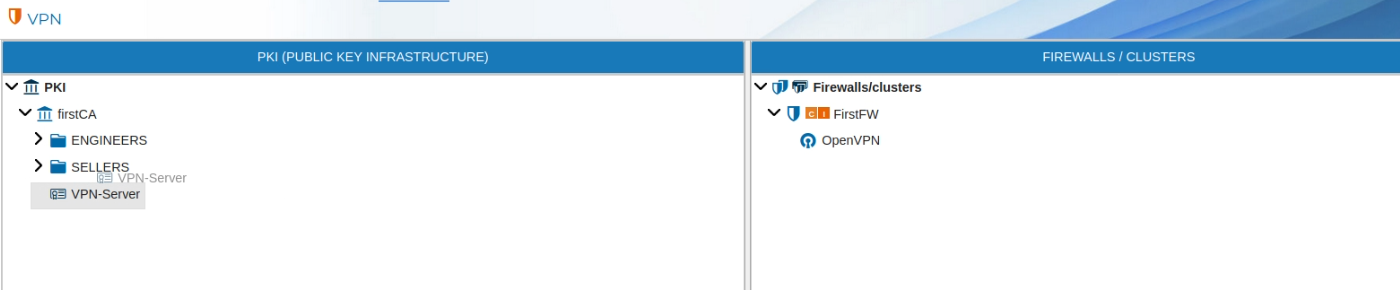
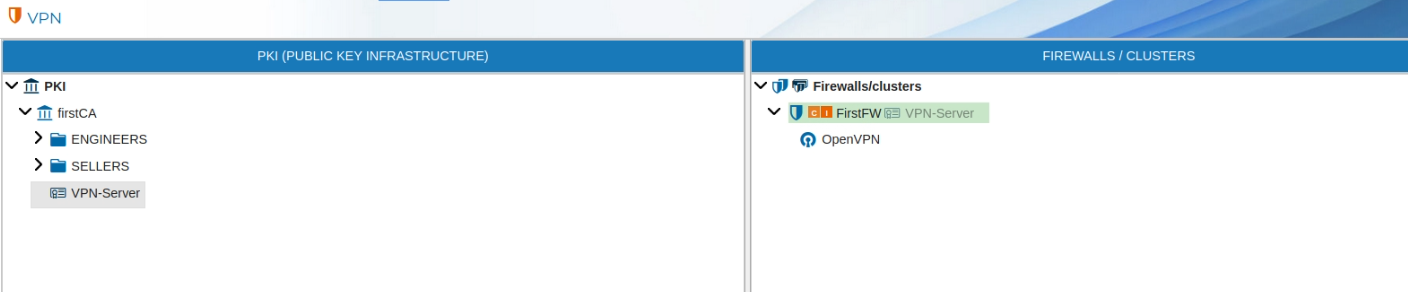
Automatically a new form is opened. You need write down the network and the mask of the network the VPN server is going to hand IP addresses from. This object is called LAN-VPN-xxxx by default, where xxxx is the name of the Sever Certificate. The name of the object can be modified if you double click the name of the Sever Certificate on the right panel or if you right click and select Edit configuration.
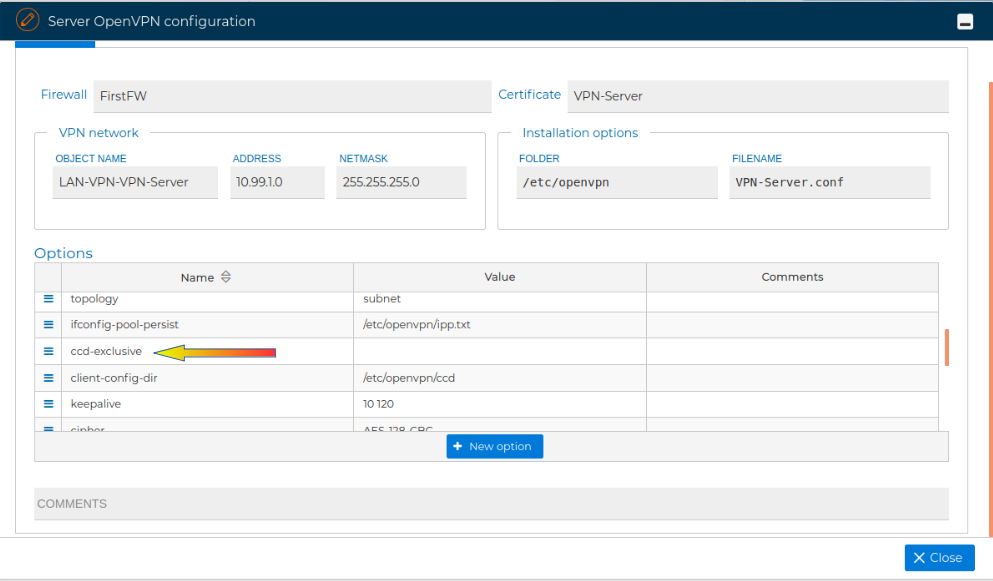
Although the configuration in this form is enough for the VPN Sever configuration you can modify these settings and modify, add or delete the allowed options, like the name of the file that will store this configuration or its folder or other options like verbosity level.
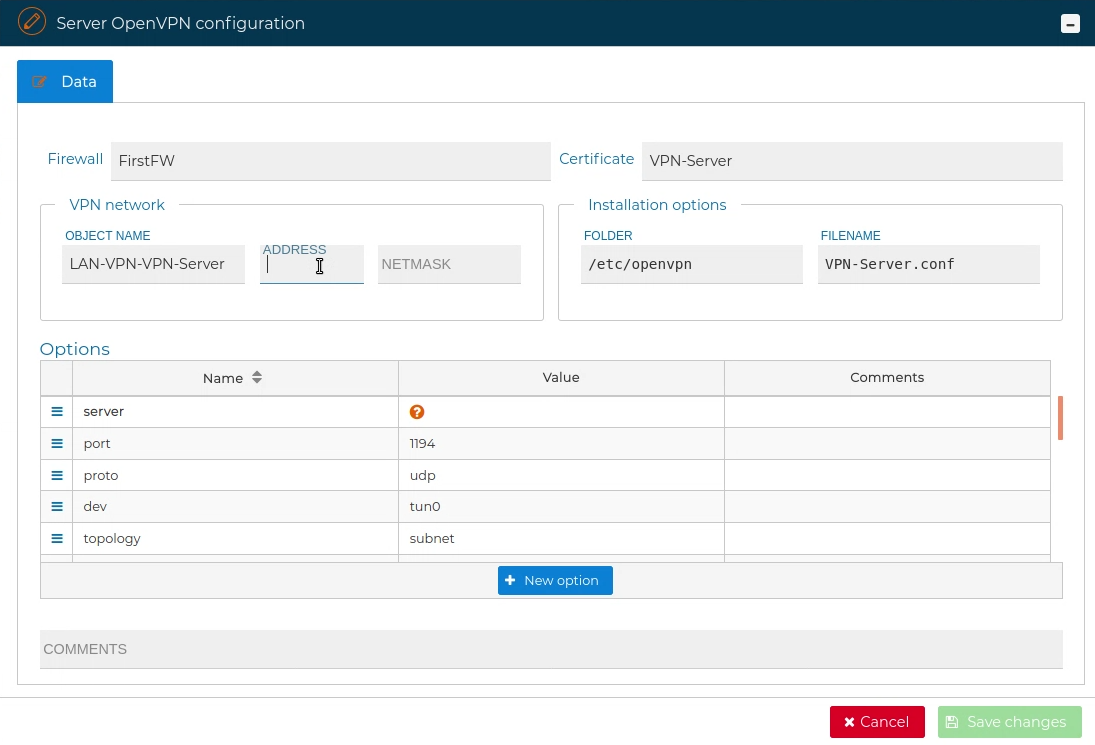
For reference, next are the allowed options: server, port, proto, dev topology, ifconfig-pool-persist, ccd-exlusive, client-config-dir, keepalive, cipher, user, group, persist-key, persist-tun, status, verb, multihome, askpass, auth-nocache, auth-retry, auth-user-pass-verify, auth-user-pass, auth, bcast-buffers, ca, ccd-exclusive, cd, cert, chroot, client-cert-not-required, client-disconnect, client-to-client, client, connect-freq, comp-lzo, compress, connect-retry, crl-verify, cryptoapicert, daemon, dev-node, dev-type, dh, dhcp-option, dhcp-release, dhcp-renew, disable-occ, disable, down-pre, down, duplicate-cn, echo, engine, explicit-exit-notify, fast-io, float, fragment, hand-window, hash-size, http-proxy-option, http-proxy-retry, http-proxy-timeout, http-proxy-server, ifconfig-noexec, ifconfig-nowarn, ifconfig-pool-linear, ifconfig-pool, ifconfig-push, ifconfig, inactive, inetd, ip-win32-method, ipchange, iroute, key-method, key, key-size, learn-address, link-mtu, local, log-appeend, log, suppress-timestamps, lport, management-hold, management-log-cache, management-query-passwords, management, max-clients, max-routes-per-client, mktun, mlock, mode, mssfix, mtu-disc, mtu-test, mute-replay-warnings, mute, nice, no-iv, no-replay, nobind, ns-cert-type, passtos, pause-exit, persist-local-ip, persist-remote-ip, ping-exit, ping-restart, ping-timer-rem, ping, pkcs12, plugin, pull, push-reset, rcvbuf, reidrect-gateway, remap-usrl, remote-cert-tls, remote-random, reneg-bytes, reneg-pkts, reneg-sec, replay-persist, replay-window, resolv-retry, rmtun, route-delay, route-gateway, route-method, route-noexec, route, rport, secret, server-bridge, show-adapters, show-ciphers, show-digests, show-net-up, show-net, show-tls, show-valid-subnets, single-session, sndbuf, socks-proxy-retry, socks-proxy, status-vesion, syslog, tap-sleep, tcp-queue-limit, test-crypto, tls-auth, tls-cipher, tls-client, tls-exit, tls-remote, tls-server, tls-timeout, tls-verify, tls-version-min, tls-version-max, tmp-dir, tran-window, tun-ipv6, tun-mtu-extra, tun-mtu, txqueuelen, up-delay, up-restart, up-cmd, username-as-commond-name and writepid. More information about the options can be found in OpenVPN options
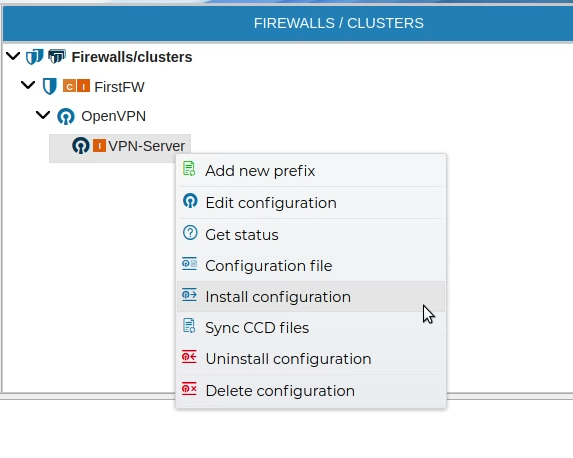
# Install Sever Configuration
Once the VPN Server configuration is created, it needs to be installed in the firewall. Right click over the server certificate and select Install Configuration.
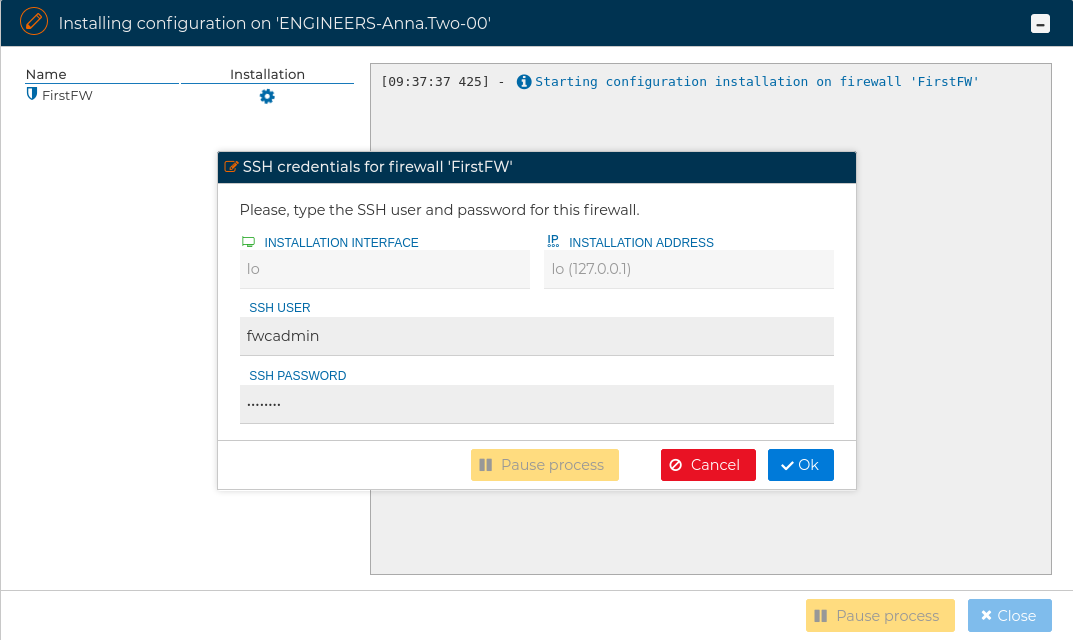
A pop up windows will ask for the credentials to access the firewall using the SSH protocol.
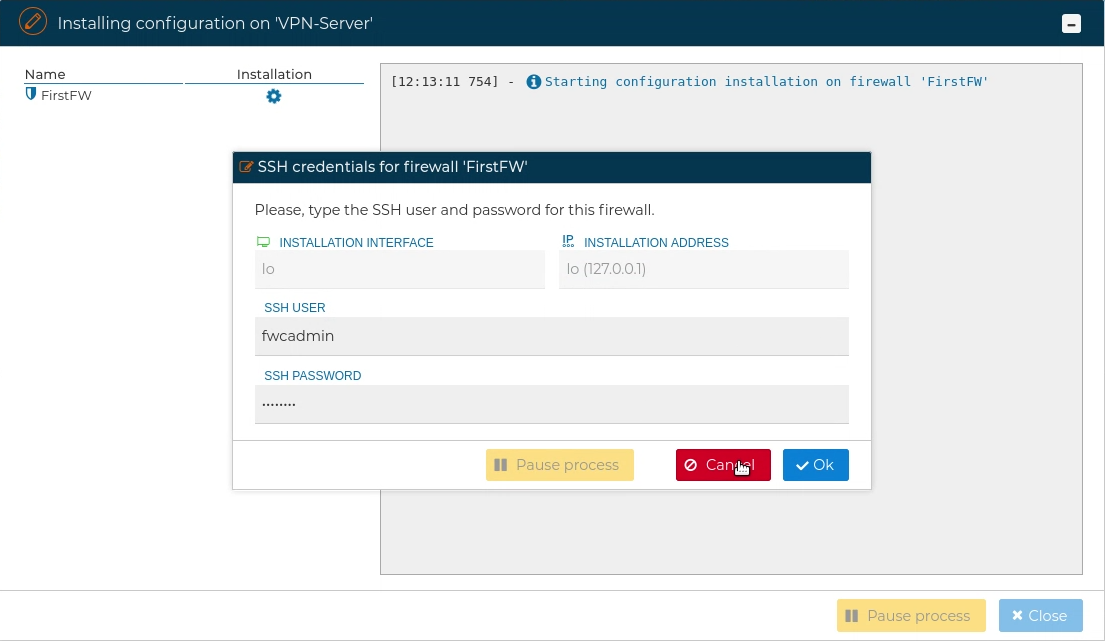
FWCloud-UI needs to have access by SSH to the firewall. The user provided also needs to be able to execute "sudo" commands, otherwise the next error will occur:
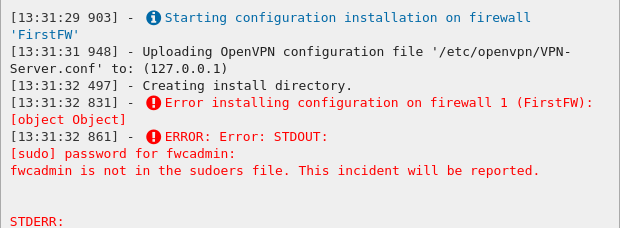
If no problems occur the VPN Server configuration will be installed on the target firewall
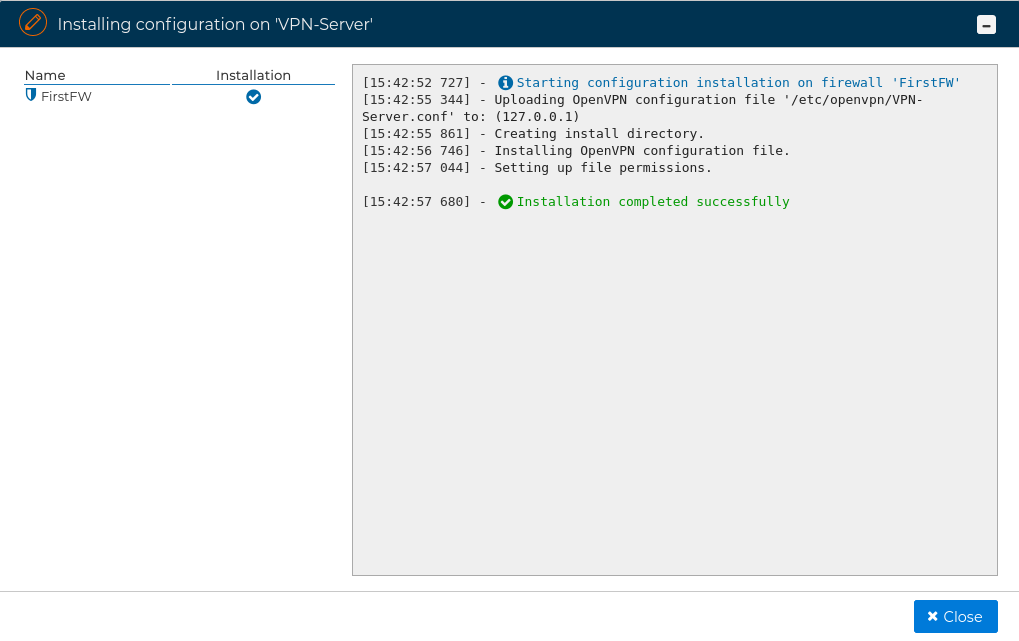
# Client Configuration
To use the client certificate drag it and drop it over the name of the VPN server. Note that the VPN server background turns green we you hover the certificate over it.
If the VPN server already has another certificate with the same name you will receive a warning and the certificate will not be moved to the server. The name of the certificates must be unique within the VPN server scope.
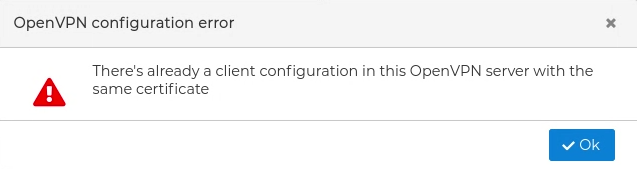
If this the first certificate you drop, automatically a new form is opened where you can configure the OpenVPN options for the client.
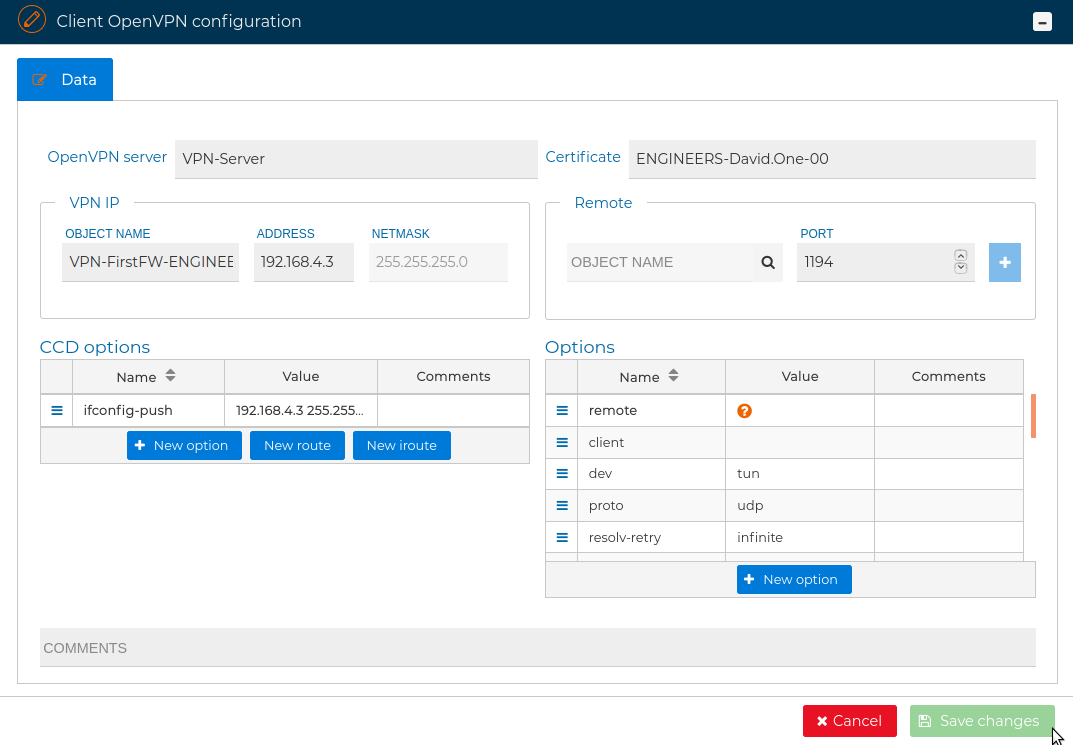
The most important option in this form you have to fill in is remote. It makes reference to the IP address the VPN clients connect to stablish the VPN tunnel. This is normally the public IP address you use to reach the firewall. You can write it in the Value field or use the magnifier  icon in the Remote section.
icon in the Remote section.
When you click that icon a new menu displays the IP addresses configured in FWCloud-UI in tree way. Select the appropriate one and click the  icon. Then modify the port if VPN server is not listening in the default one and finally click on the
icon. Then modify the port if VPN server is not listening in the default one and finally click on the + icon next to the port number.
More than one remote option can be added and they will be used sequentially to connect if the others fail to connect.
In the VPN client configuration form you can also add delete or modify other options like: remote, client, dev, proto, resolv-retry, nobind, user, group, persist-key, persist-tun, chipher, auth, auth-nocache, tls-client, verb, float and remote-cert-tls.
If routes needs to be pushed to the client or added in the server, this can be done using the CCD options that are included in the bottom left side of this form.
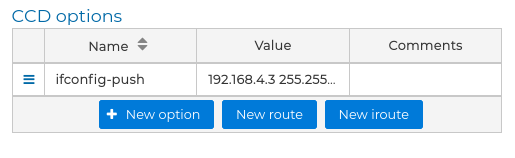
The options available here are: push, push-reset, iroute, iroute-ipv6, ifconfig-push, ifconfig-ipv6-push, disable, config, max-routes-per-client and comp-lzo.
As the most used options in this section are push and iroute, there are two buttons that simplify the work.
If you push New route button you get a piece of the FWCloud-UI object tree where you can select the IP or network addresses configured in FWCloud-UI. Then the push option will be added with the selected address and with the proper network mask configured. The same is for the New iroute button. Note that the syntax of these options is different.
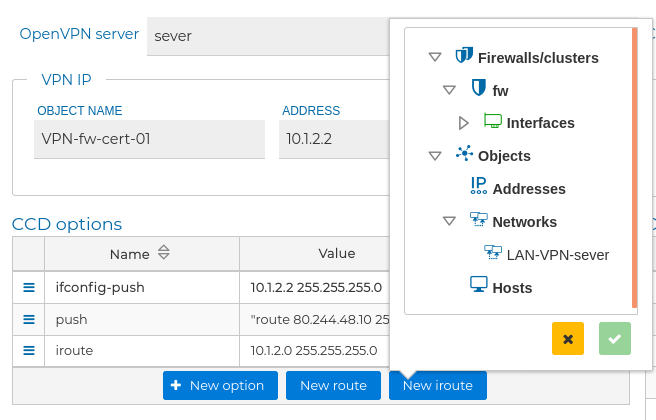
When you have the VPN client configuration ready press Save changes button in right bottom side of the form. The new client certificate appears in the FIREWALLS/CLUSTER side with an  icon by his name. This indicates this certificate is not yet installed in the firewall.
icon by his name. This indicates this certificate is not yet installed in the firewall.
When you drop the client certificate in the VPN server, if this already have other client certificates you will be asked if you want to clone the configuration from another client VPN configuration.
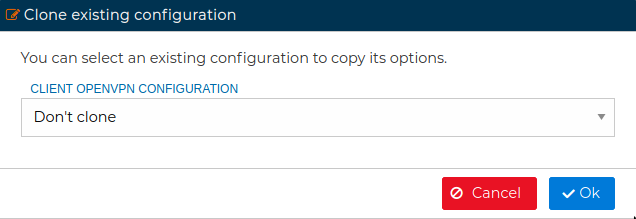
In this form you can choose from the drop down field which client configuration you want to copy its options from. When you are configuring multiple clients this save you a lot of time and avoid mistakes. After that the client configuration form will be opened.
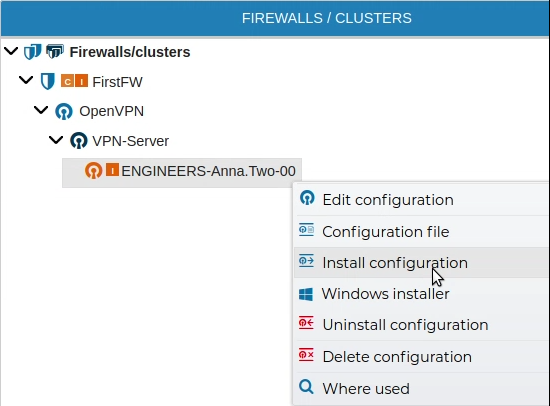
# Install Client Configuration
Once the VPN Client configuration is created, it needs to be installed in the firewall. Right click on the client configuration name and select Install Configuration.
A pop up windows will ask for the credentials to access the firewall.
When the certificate is installed in the firewall the  icon by his name will be cleared.
icon by his name will be cleared.
# Prefixes
Prefixes can also be created in the FIREWALL/CLUSTER section.
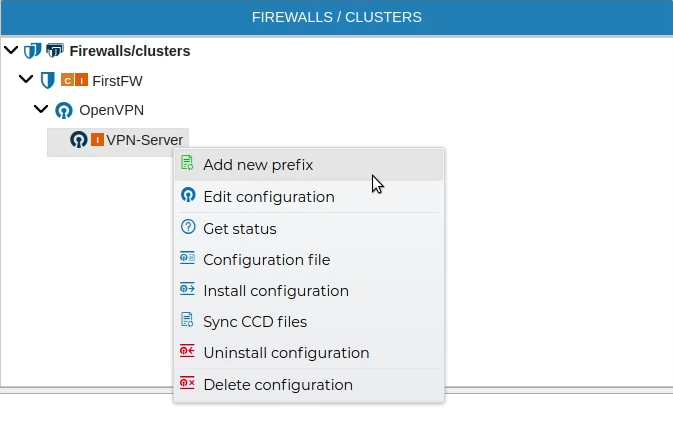
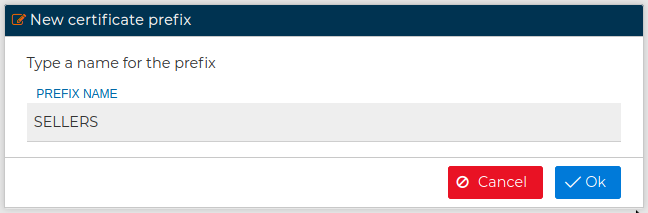
Do not confuse with PKI prefixes
PKI prefixed are for organizational purposes only while OpenVPN server prefixes can be used in the security policy.
In the next figure you can see PKI prefixes on the left side are represented by ![]() while the prefixes created in the OpenVPN server have a different
while the prefixes created in the OpenVPN server have a different ![]() icon.
icon.
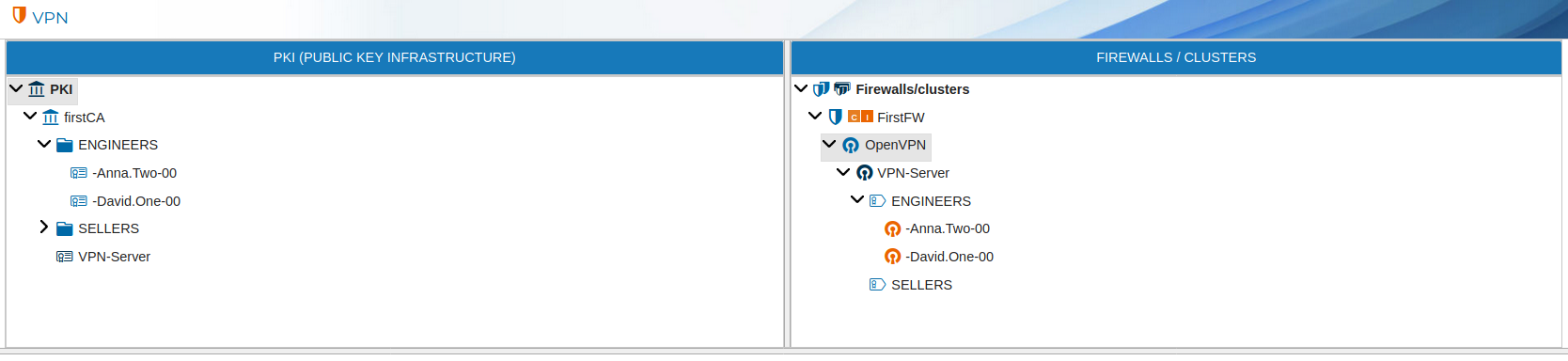
You can use the Prefix when creating the policy rules. Instead of needing to add all IP addresses of every VPN connections of any client which his certificate name starts with a common part (the prefix), you can add that Prefix in the rule. The prefix can be dragged and dropped in the rule fields. FWCloud-UI will display the prefixes in the Policy section when you expand the OpenVPN branch inside the firewalls in the Firewalls group.
Only OpenVPN server prefixes will be displayed here.
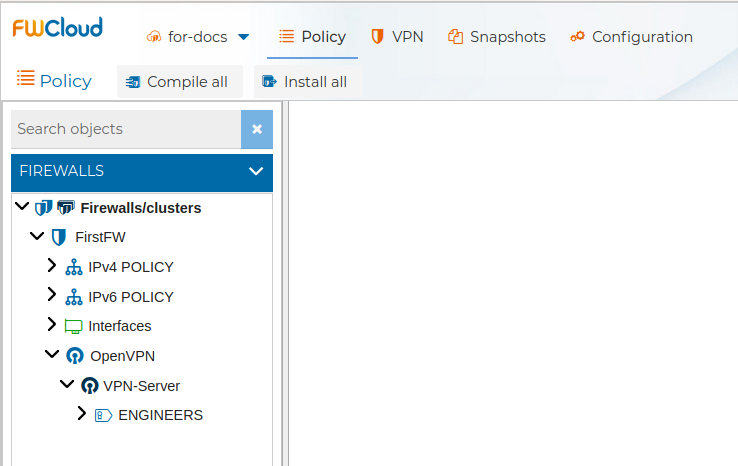
Here you have an example with two rules using prefixes
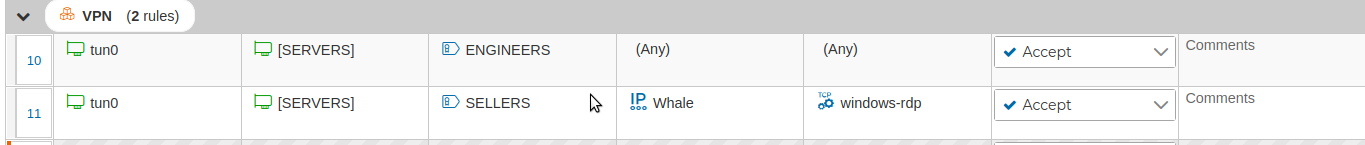
In this case since we have two VPN client configurations with the prefix ENGINEERS, the rule number 10 refers to any connections established from this two VPN clients
The use of prefixes makes the security policy more clear and easy to read. Also when you create new VPN client configurations with the same prefix you do not need to modify or create new rules. Although the policy needs to be compiled and installed again, since when it was installed in the firewall it did not yet have the new clients configurations.
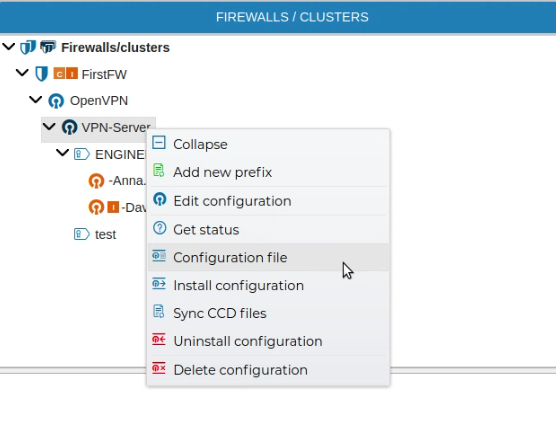
# Server Config File
Although the VPN server configuration can be installed on the firewall from the FWCloud-UI, also you can get access to the file that stores this configuration, just right click and select Configuration file.
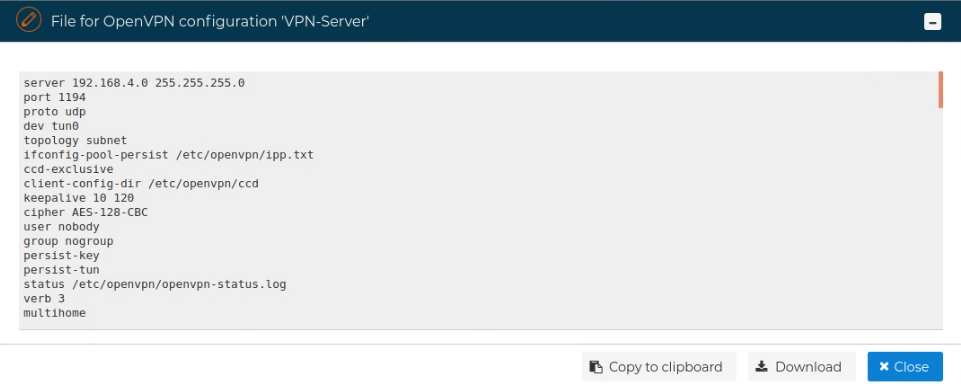
A new form is opened where you can download or copy the content of the file to the clipboard.
# Clients Config File
The configuration file of the VPN clients can also be obtained by right clicking on the client configuration name and select Configuration file.
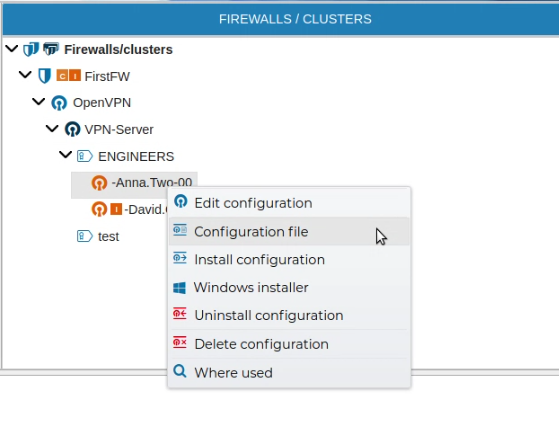
A new form is opened where you can download or copy the content of the file to the clipboard.
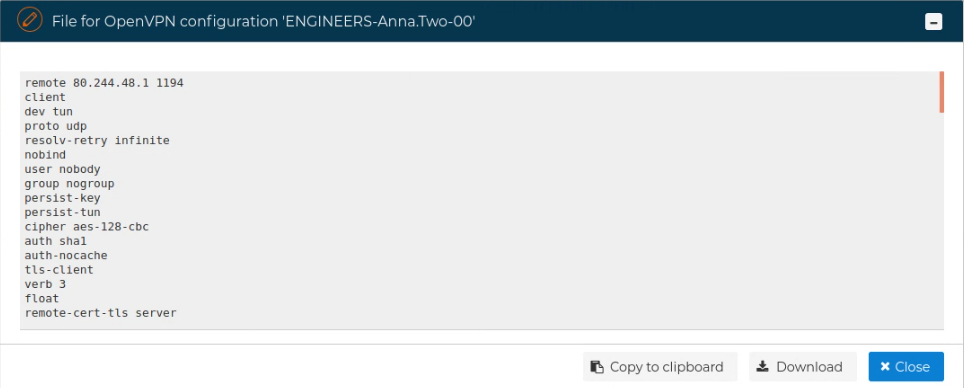
If you copy it to the clipboard a popup message in the right top corner will indicate when the copy has finished.

This file will be needed if you want to install the a VPN connection in the client equipment. This configuration file is ready to be use with the majority VPN client programs like Tunnelblick on OSX based systems or OpenVPN-Gui on Windows based systems.
For Windows based systems you can use the FWCloud-UI Windows installer feature that will provide an installer that bundles the VPN client program and the configuration file.
# Edit Configurations
In order to edit the VPN server configuration right click on the VPN server name and select Edit configuration.
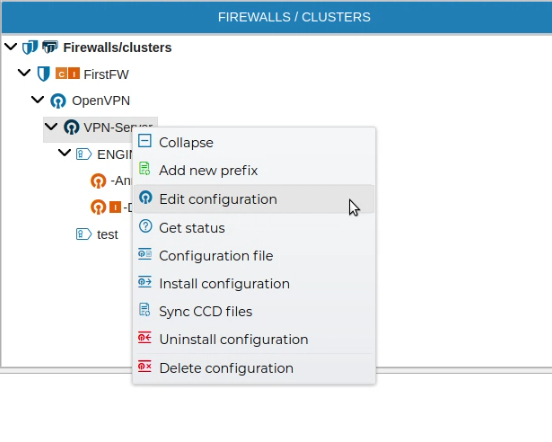
The configuration form for the server is opened and you can make any notifications to it.

Also the VPN configuration of a client can be edited if you right click on the client configuration name and select Edit configuration.
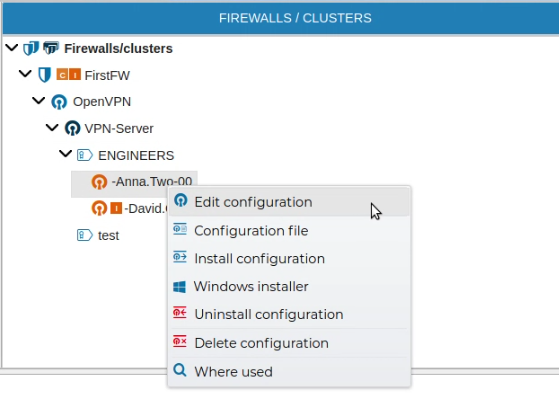
The configuration form for the client is opened.
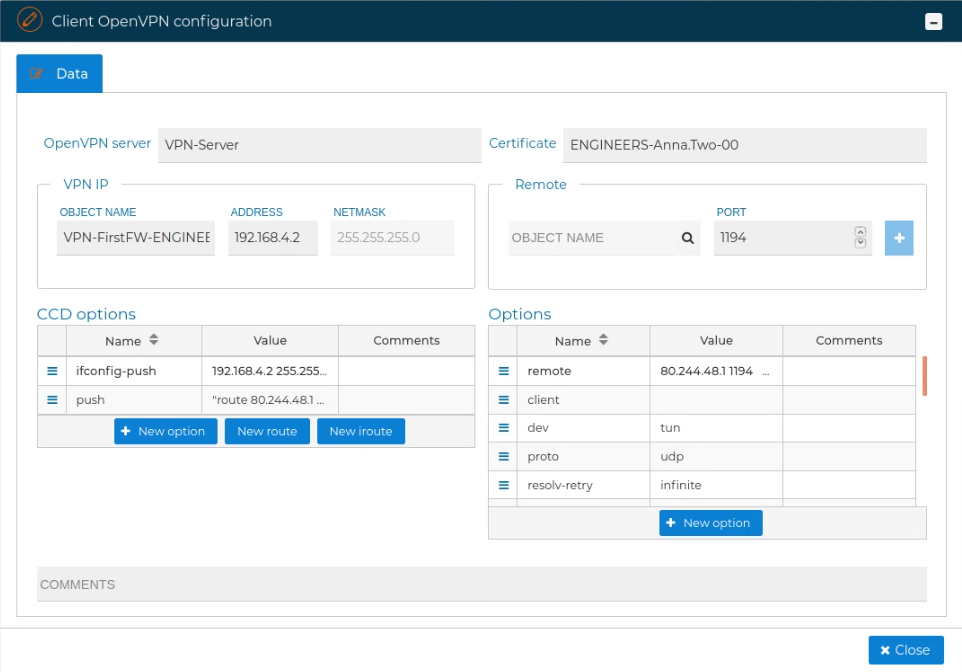
# Synchronize CCD files
You can reinstall all client VPN configurations into the VPN server.
This option is useful if you have several client configurations pending to be installed.
# Block / Unblock Client Configurations
When a VPN connection is not going to be used for a temporal period it can be blocked, not allowing the connection to be established
The process will install the CCD in the server to start to blocking the connection. If the password of the the firewall is not stored it will be required.
A message informs the connection has been successfully blocked:

VPN connections blocked are displayed in gray text and the icons change to reflect that.
Any blocked VPN connection can the unblocked from the context menu:
Again the modified client configuration will be installed in the firewall, and a message will inform it has been unblocked:

# Uninstall Configurations
The VPN server configuration can be uninstalled from the firewall. All client configuration of the VPN server must be uninstalled first.
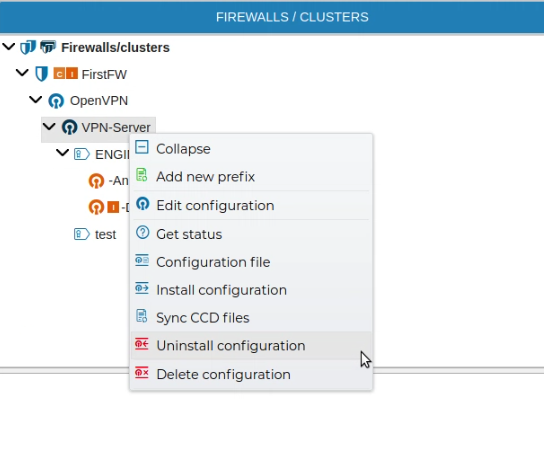
FWCloud will check if there are client configurations for the server configuration. In that case it will not proceed and will show an error message.
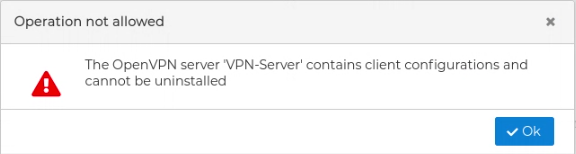
To uninstall a client configuration, right click over the name and select Uninstall configuration.
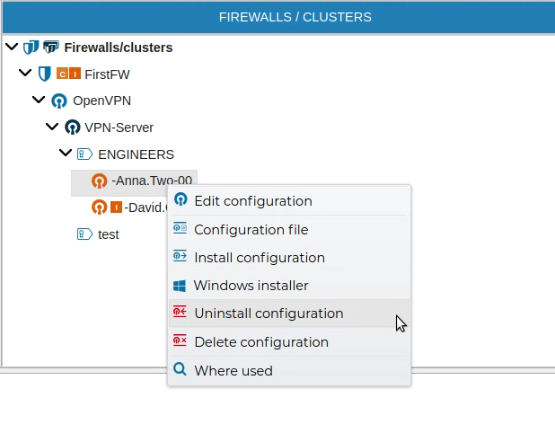
FWCloud-UI will ask for the credentials to access the firewall.
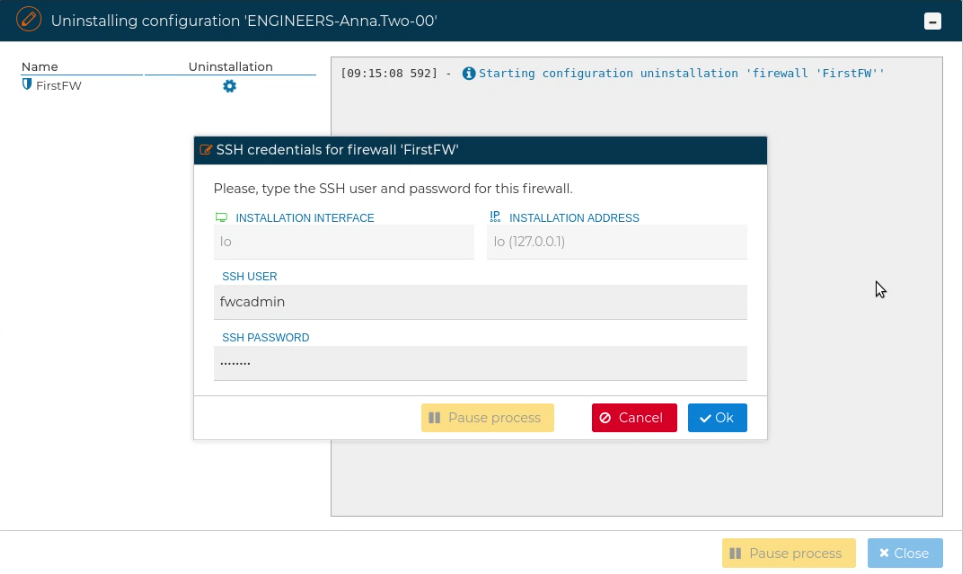
If the ccd-exclusive option is configured in the OpenVPN server, when a VPN client configuration is unstalled that client will no longer be able to connect to the VPN server. This option is configured by default when an OpenVPN server is configured in FWCloud-UI.
This a very fast and ease way to block a VPN user.
# Delete Configurations
If a VPN configuration is no longer needed it can be removed. This can be done from the context menu of the configuration name. Right click and select Delete configuration.
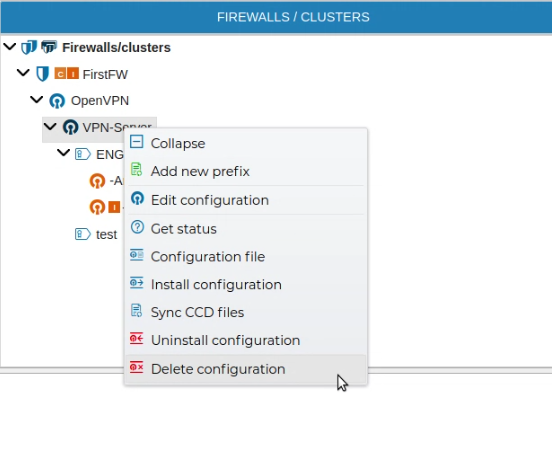
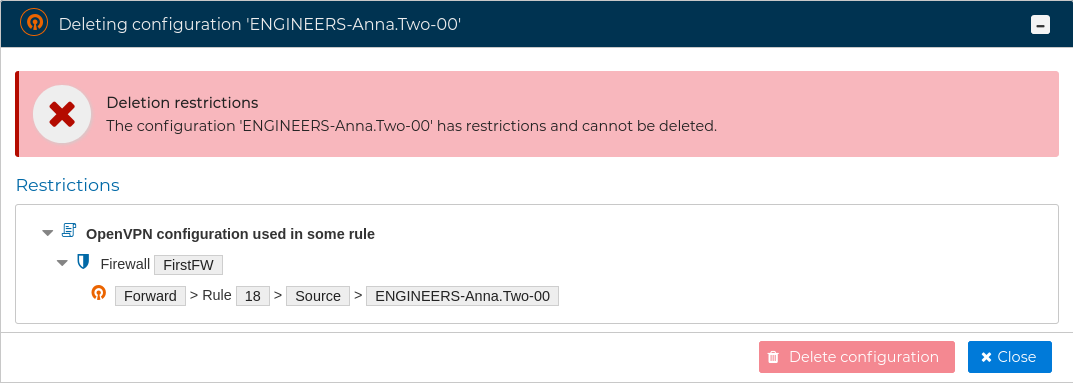
A server configuration can only be deleted if there are no client configurations. FWCloud will detect if client configurations exist.
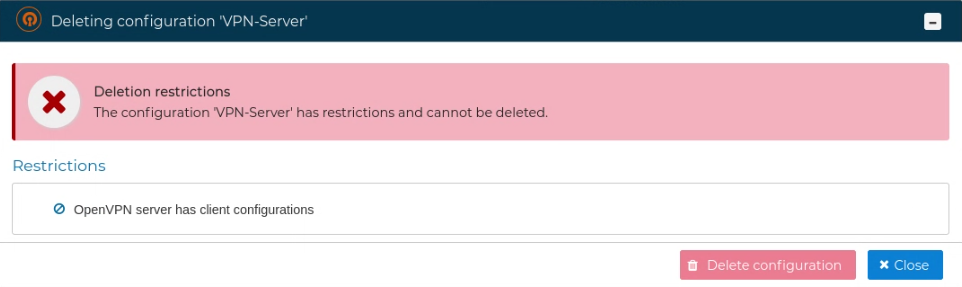
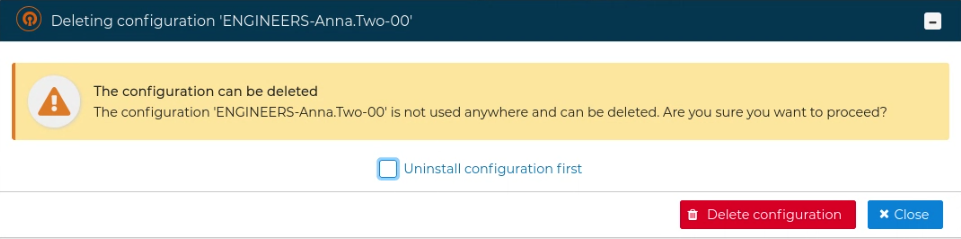
To delete a client configuration select Delete configuration from the client context menu.
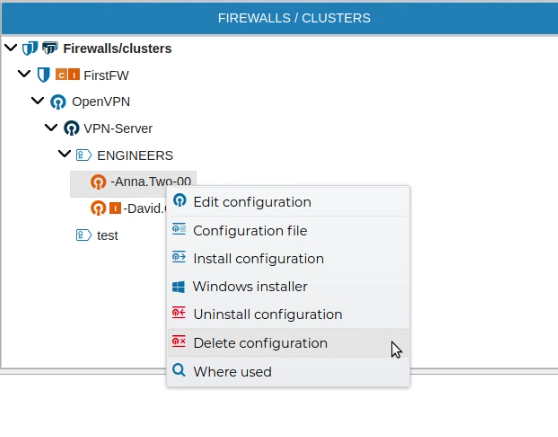
Again FWCloud will check first if there is any conflict that not allows the deletion and it will warn if that is the case.
You can uninstall the configuration first and remove it later or do both actions at the same time by marking the box Uninstall configuration first.
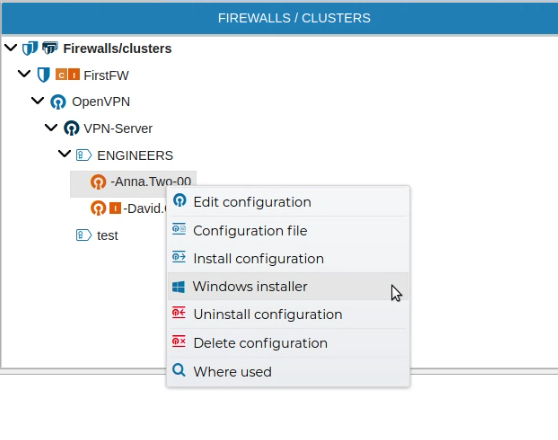
# Windows Installer
Directly from the VPN client configuration you can obtain a wizard that will guide you installing a VPN client on Windows systems. Select WindowS installer.
FWCloud-UI will generate a Windows executable program for the selected client. By default it is name after the client connection name by you can modify this name, then press the bottom Generate file to continue.
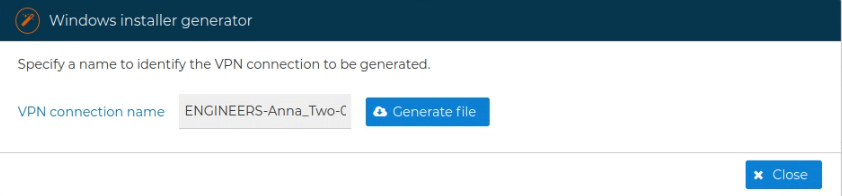
A new form indicates the generation is in progress.
Once the program it is ready it will be automatically downloaded from your browser.
Save this program and copy in the Windows computer you want to install the VPN client connection. For the installation process no Internet access is required. Just execute the generated installer and click next. It will guide you screen by screen. This program will install or upgrade OpenVPN-GUI and create a new VPN connection for the client it was generated for against the VPN server. It will ask if you want to run it after the installation is finished.
# VPN Status
FWCloud allows you to see the status of the VPN connections established in the firewalls.
To do this you must go to the VPN tab and in the "FIREWALLS / CLUSTERS" section, on the right of the screen, right click on the VPN server you want to see the connections for and select Get status.
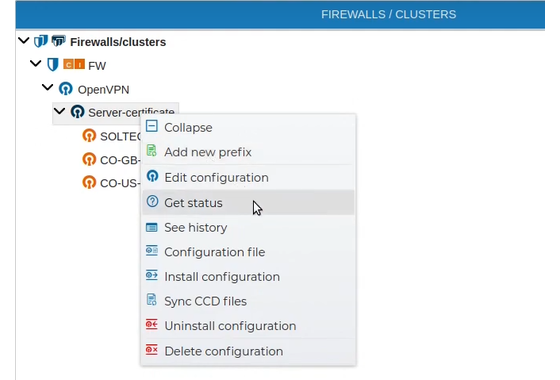
At the bottom of the screen all the active connections at the current moment will be shown. At the bottom left there is a table indicating the common name (CN), the virtual IP address assigned to the VPN connection, the real IP and the port used, the traffic received, the traffic sent and the date on the the connection was established. The rows can be sorted by any of the fields displayed by clicking on the column name. The content of the table is dynamic and changes depending on whether the VPNs are connected or disconnected on the analyzed server.
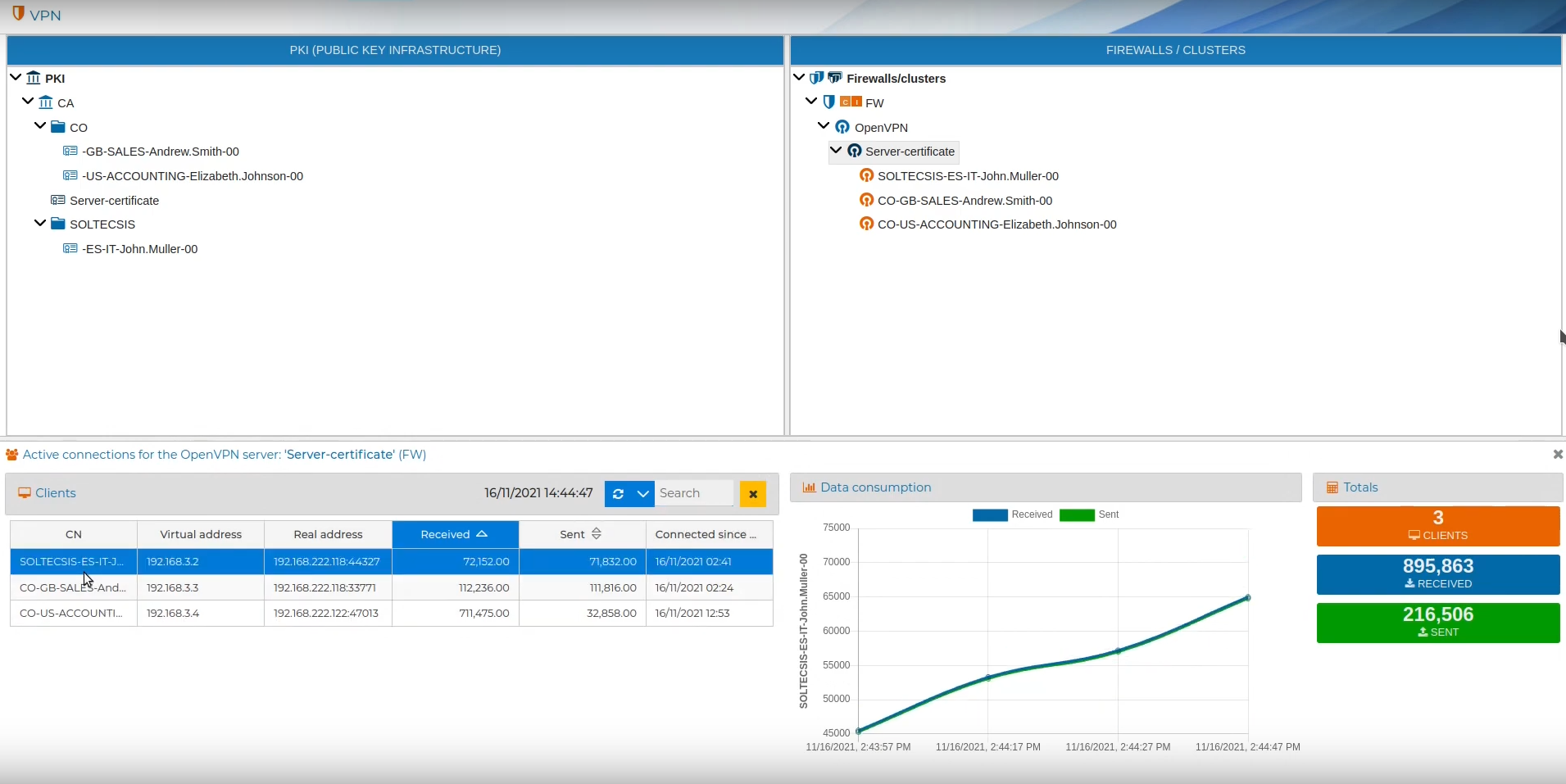
On the right side next to the table the status of the connection selected in the table is graphically represented. In the graph we have two curves, one for the traffic sent and the other for the received. The graph is updated according to the refresh period.
Further to the right we have 3 boxes indicating the values of the total number of connections and the total traffic received and sent.
It is possible to configure the update period of the table or deactivate it completely by clicking the  button.
button.
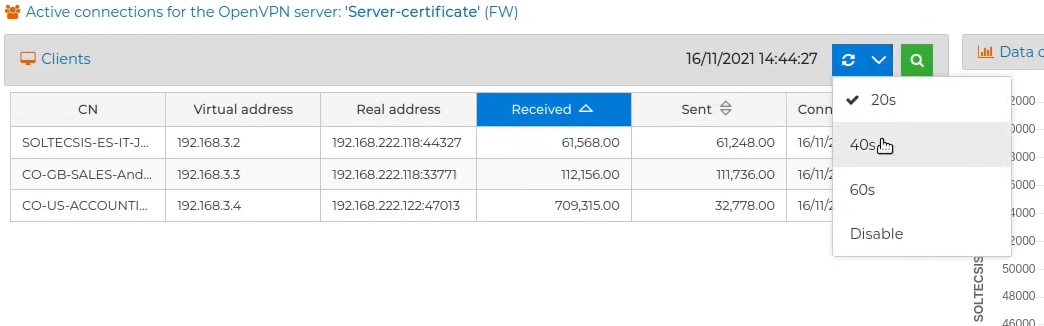
Likewise, you can force an immediate refreshment by clicking ![]() button
button
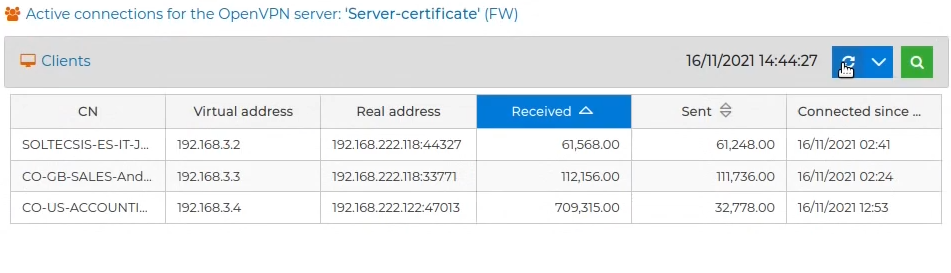
In the event that there are many established connections, it is convenient to filter the results by some common pattern, for example parts of the CN. When naming VPN connections, we recommend that they start with the name of the company, followed by a dash, the country, dash, department name, dash, full name of the person or employee who uses it, dash and finally, a numeric identifier to be able to distinguish between them in the case of having more than one for the same employee.
To filter the results, click on  and write the pattern in the text field.
and write the pattern in the text field.
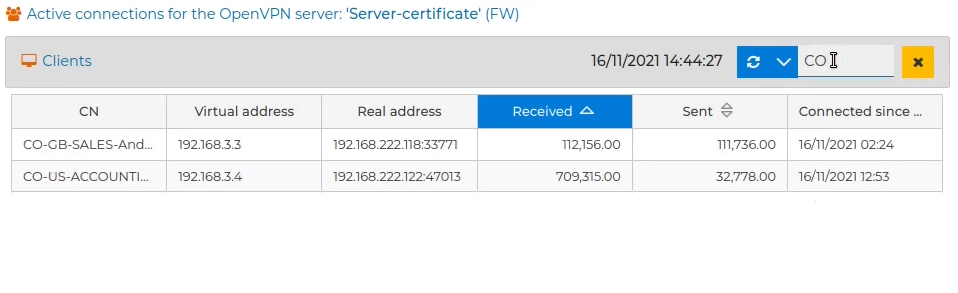
# VPN Connection history
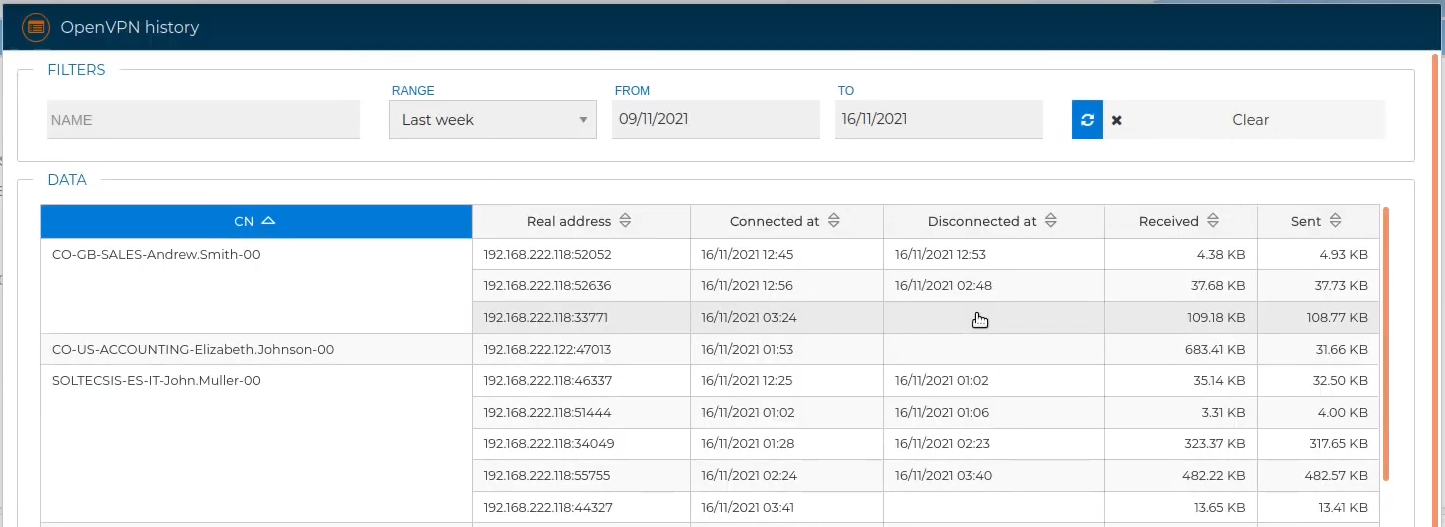
To analyze a specific problem, sometimes it is useful not only to see the current state of the connection, but also its connection history.
Thanks to the FWcloud-Agent , this information is periodically collected and stored in the FWCloud database, so that it is available for later consultation, even if the connection between FWCloud and the analyzed firewall is not possible at that time.
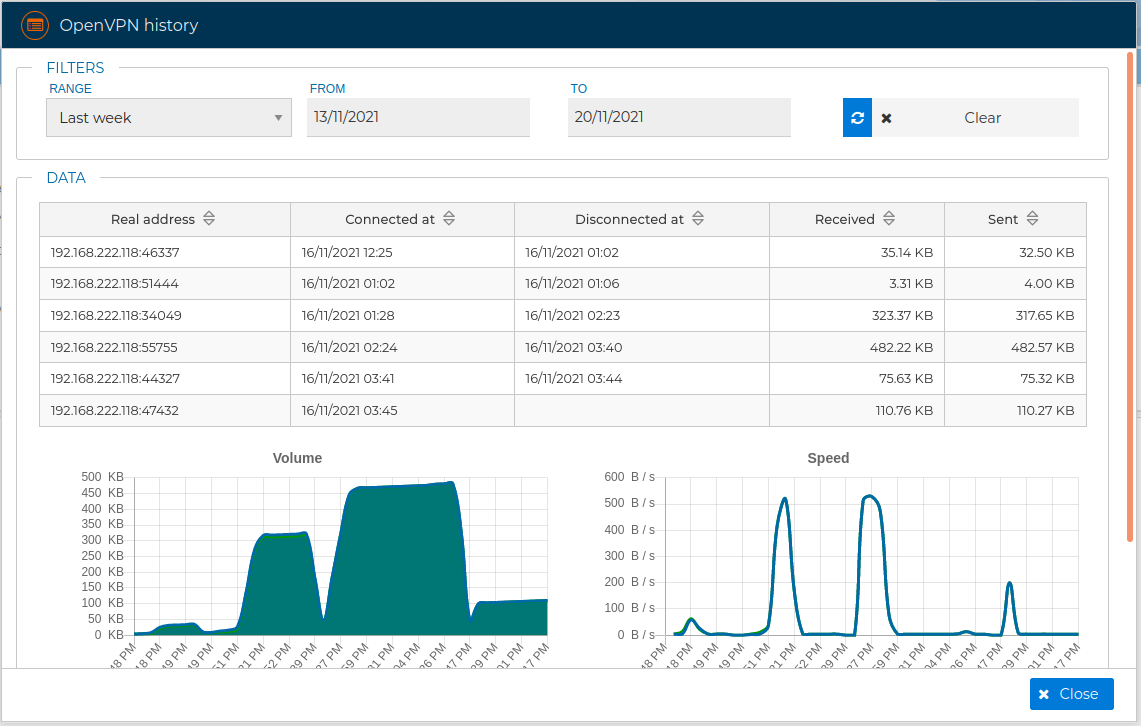
You will see a table with the history of all VPN connections. We can order the table by clicking on any column name. Next the VPN connections are ordered by Name.
If you scroll down the pane at the bottom of the table there are two graphs representing the traffic Volume and the Speed of the VPN connections.
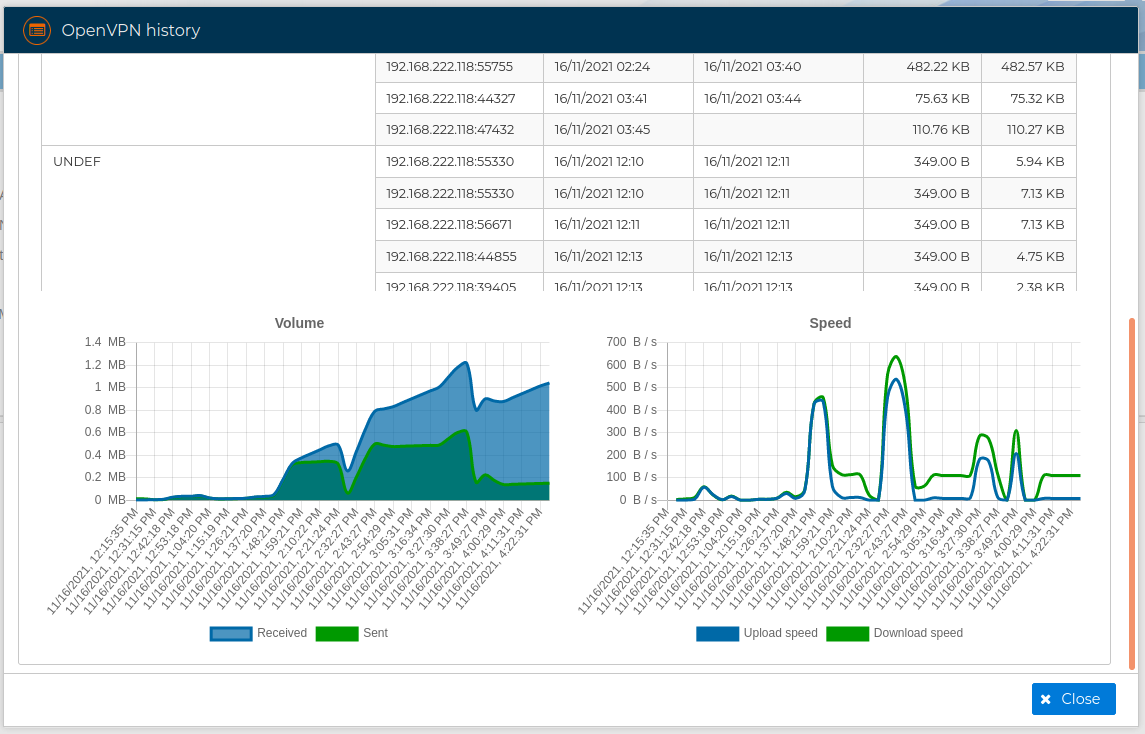
The results can be filtered by the VPN connection name:
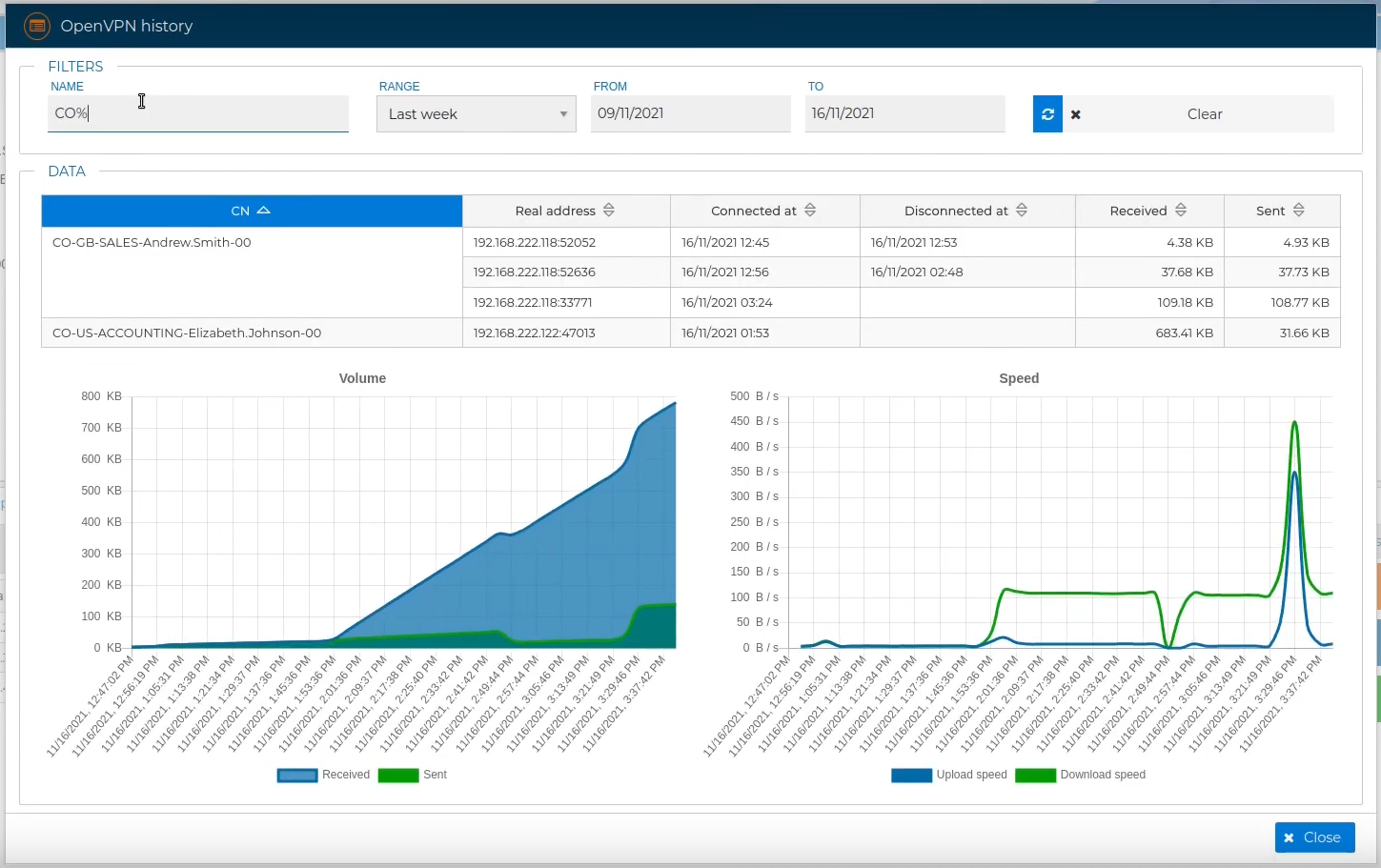
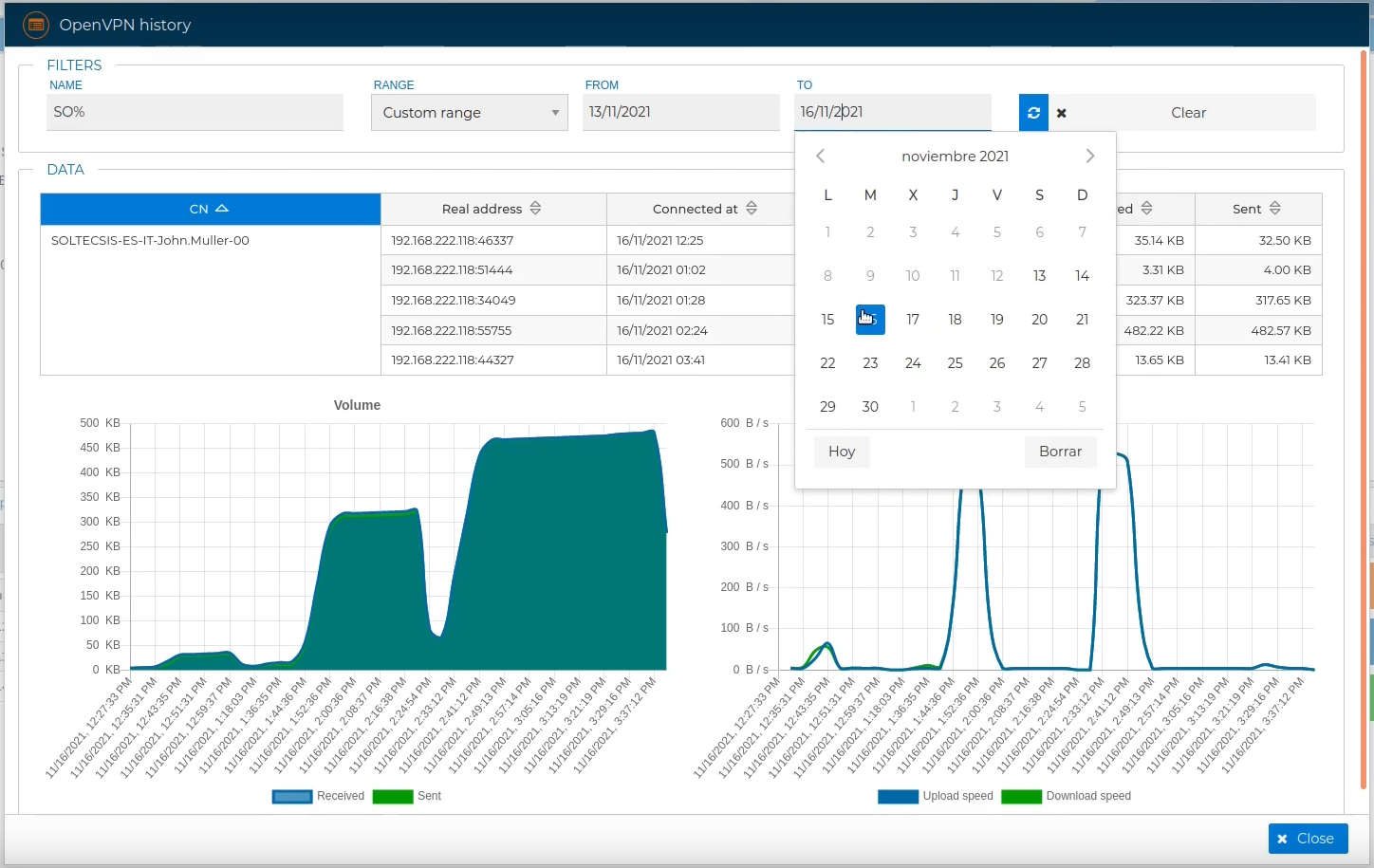
The data can be shorted by selecting a specific period like 'Last day', 'Last week', 'Last month' or a 'Custom rage'. In the last case you can pick the starting and the ending day of the period to be showed.
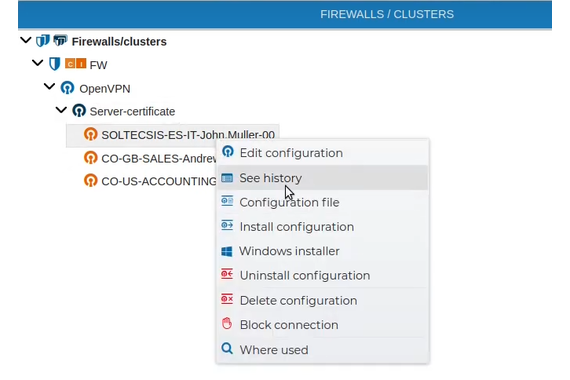
If you are interested only in the connection history of a specific VPN, you can obtain this information directly from the contextual menu of the connection and thus not have to filter the results by the name of the connection.
You can also select the appropriate interest period using the form fields described above.
To speed up the work, both the obtaining of the status of the VPN connections and their history can be consulted directly from the "Policy" panel in which the policy rules are configured. Just look for the VPN server or individual connections in the hierarchical structure on the left by following the path "FIREWALLS" - <Name of the firewall or cluster> - "OpenVPN" - <VPN server> [- <VPN connection>] and press with the right button to obtain the contextual menu and select the option "Get status" or "See history" as appropriate.
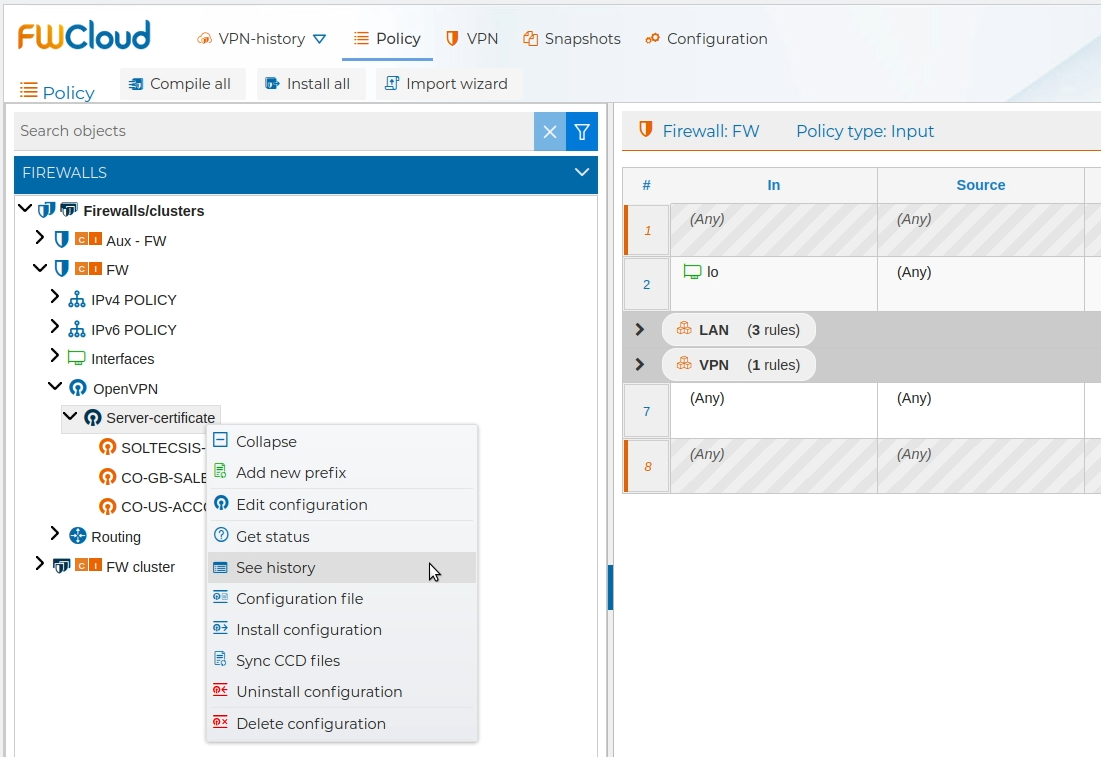
Below you can watch a video showing the use of VPN connection history:
# VPN Connection history archiver
In certain cases, if we have firewalls with a large number of VPN clients connecting and disconnecting, the information collected and stored can be quite high. By default, information corresponding to 180 days is stored in the FWCloud database. This is configurable by editing the properties of FWCLoud.
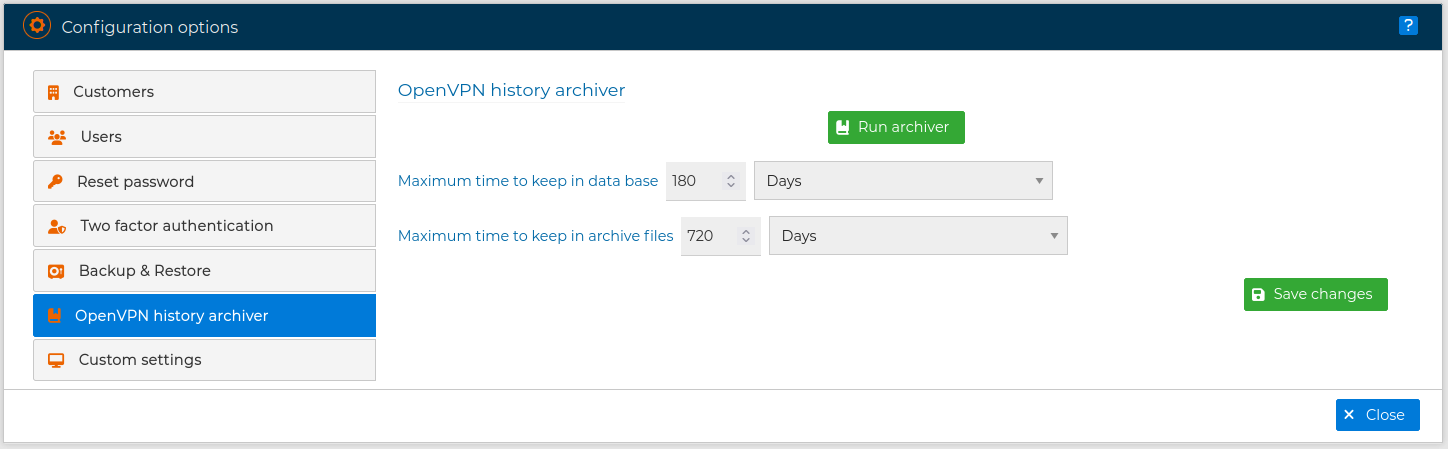
Information older than specified is stored in files. In order to control the occupation of disk space, we can modify the time we want to store this information. The default value is 720 days.
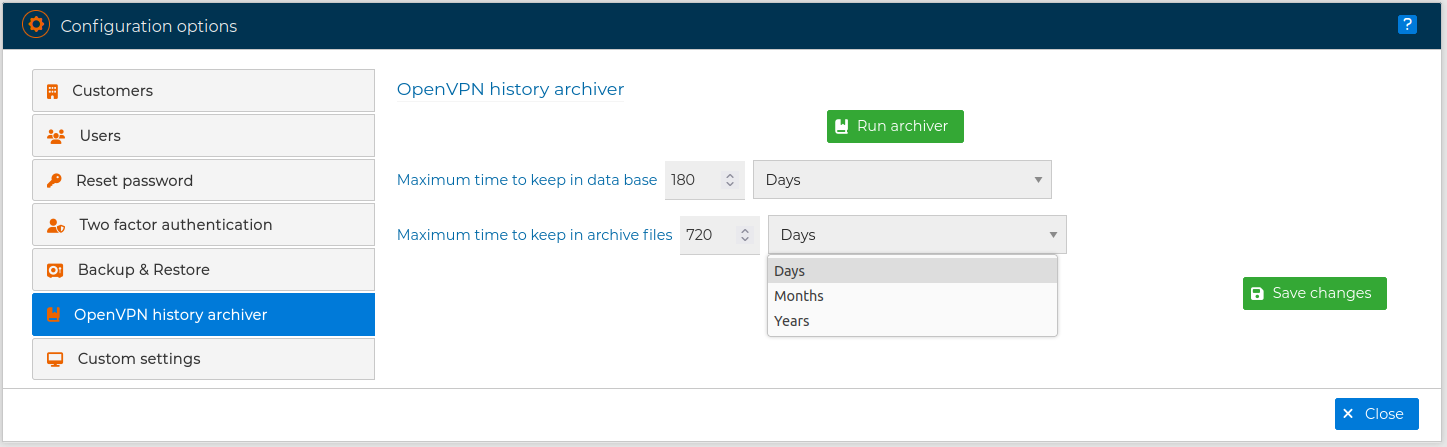
Also from this same form you can force a manual archive by pressing the Run archiver button
