# Plugins
Plugins are third-party software products that can be installed to extend the functionality of the firewalls. We can access the Plugins section directly from the context menu of the firewalls.
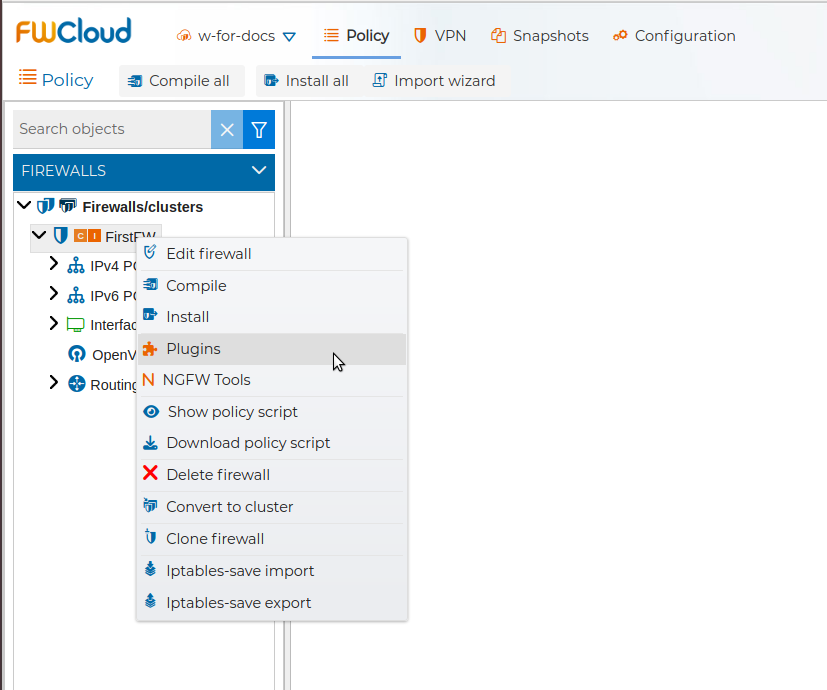
Or by editing the firewall settings and going to the tab named Plugins. This tab will be active only if the communication method with the firewall is FWCloud-Agent.
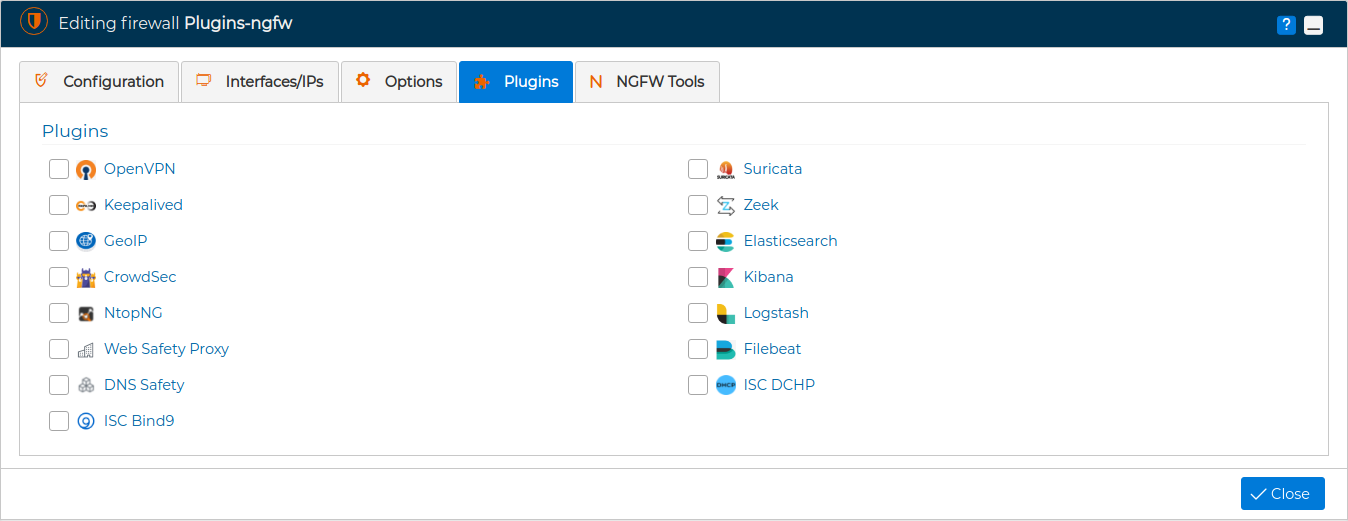
Despite not being part of FWCloud, we can control the installation of these security products from FWCloud-UI. Installing or uninstalling them basically consists of checking or unchecking the corresponding box. You can see a video about this functionality:
In addition on some of the plugins we can also manage the configuration from FWCloud-UI.
Let's briefly describe these products:
# OpenVPN
 | OpenVPN (opens new window) |
|---|
OpenVPN is the name of the open source project that provides secure access to your private, cloud, or on-premises business network. It allows you to create secure point-to-point or site-to-site connections in routed or bridged configurations and remote access installations. It implements both the client application and the server application.
For more information on the use of OpenVPN in creating and maintaining VPN connections, see the VPN section of this manual.
The OpenVPN protocol emerged to establish itself as a de facto standard in the open source networking space with over 50 million downloads.
You can watch the following video in which a basic configuration of an openvpn installation is briefly installed and created:
# Keepalived
 | Keepalived (opens new window) |
|---|
Keealived's goal is to provide simple and robust installations for load balancing and high availability for Linux system and Linux-based infrastructures.
Keepalived provides frameworks for both load balancing and high availability. Load Balancing is based on the Linux Virtual Server (IPVS) kernel module, which provides layer 4 load balancing. Keepalived implements a set of health checkers to dynamically and adaptively maintain and manage pools of servers with load balance according to its status. While high availability is achieved by Virtual Redundancy Routing Protocol (VRRP)
# GeoIP
 | GeoIP (opens new window) |
|---|
GeoIP are a series of products, from MaxMind, that allow discovering information related to the geographic position of a specific IP address. We can use GeoIP databases, that are are regularly updated, to find the country an IP address or hostname originates from. The GeoIP lookup program will return the country in which the indicated IP address is located.
They allow us to have an approximate geographical vision of what is going on in the network connections that we are studying.
The data can be used to identify high-risk activity in eCommerce payments, platform user activity, incentivized traffic, and more.
As more of the world adopts a privacy-focused approach to web usage, IP geolocation fills an essential niche in customer analytics.
We have a video where we mention this plugin to take advantage of the use of references to countries and continents in the security policy rules of a firewall.
# CrowdSec
 | CrowdSec (opens new window) |
|---|
CrowdSec is a free, modern, collaborative behavioral detection engine coupled with a global IP reputation network. It's a lightweight open source software that allows you to detect peers behaving maliciously and block them from accessing your systems at various levels (infrastructure, system, application).
To achieve this, CrowdSec reads logs from different sources (files, streams...) to analyze, normalize and enrich them before comparing them to threat patterns called scenarios. Use the strength of the community to detect and stop attacks in real time based on your logs, allowing you to preemptively block known bad guys from accessing your information system.
# NtopNG
 | ntopng (opens new window) |
|---|
ntopng is the next generation version of the original ntop, a network traffic probe that monitors network usage. ntopng is based on libpcap/PF_RING and it has been written in a portable way in order to virtually run on every Unix platform, MacOS and on Windows as well.
It provides a intuitive, encrypted web user interface for the exploration of realtime and historical traffic information. This interface is accessible using port 3000. Let's say the firewall we have installed has the IP address 192.168.1.1, we just have to point our browser to http://192.168.1.1:3000/
# Web Safety Proxy
 | Web Safety Proxy (opens new window) |
|---|
Web Safety is a deep content inspection proxy that has access to actual contents of HTTP requests. This allows it to decrypt, secure and re-encrypt both incoming and outgoing TLS traffic. Questionable content is blocked easily.
Intercepted browser request and remote site response get into Web Safety Proxy, are analyzed and access is allowed or denied based on configured policy settings by de administrator. Information about request and response is stored in the database.
We access the administration web interface using the URL https://192.161.1.1:8095/ (replacing the IP address for the one that corresponds to our firewall).
# DNS Safety Proxy
 | DNS Safety Proxy (opens new window) |
|---|
DNS Safety filter is a DNS forwarding server (like dnsmasq, unbound, pi-hole) with extensive filtering capabilities. It allows administrator to filter access to domain names by categories, easily block access to user specified domains and provides different access policies for different groups of machines in your network.
DNS Safety is supposed to be deployed as primary DNS server in your local network and can forward DNS requests to your ISP's DNS server, Google Public DNS, OpenDNS and other third party DNS providers. Internal DNS requests can be forwarded to internal DNS servers (for example Active Directory domain controllers).
The management interface is accessible through https://192.161.1.1:8096/ (changing the IP address).
# ISC Bind9
 | ISC Bind9 (opens new window) |
|---|
In the plugins section you can activate ISC Bind9. Almost any Internet connection requires domain name resolution. If the configuration of a DNS server has been considered, you can use FWCloud to facilitate this task. ISC Bind9 is an open source DNS system licensed under the MPL 2.0 license and supported by a large community.
# Suricata
 | Suricata (opens new window) |
|---|
Suricata is an open source cybersecurity tool used to monitor system network traffic and is capable of detecting malicious behavior. Suricata was developed and is currently maintained by OSIF (Open Information Security Foundation), a non-profit organization that is committed to keeping Suricata open source forever.
Suricata can log HTTP requests, register and store TLS certificates, extract files from streams and store them on disk. Full pcap capture support allows for easy analysis. All of this makes Suricata a powerful engine for your Network Security Monitoring (NSM) ecosystem.
Suricata implements a comprehensive signature language to match known threats, policy violations, and malicious behavior. It detects anomalies in the traffic it inspects. i
# Zeek
 | Zeek (opens new window) |
|---|
Zeek has a long history in the open source and digital security worlds. Vern Paxson began developing the project in the 1990s under the name “Bro”.
Zeek is not an active security device, like a firewall or intrusion prevention system. Rather, Zeek sits on a “sensor,” a hardware, software, virtual, or cloud platform that quietly and unobtrusively observes network traffic.
Zeek interprets what it sees and creates compact, high-fidelity transaction logs, file content, and fully customized output, suitable for manual review on disk or in a more analyst-friendly tool like a security and information event management (SIEM) system.
# Elasticsearch
 | Elasticsearch (opens new window) |
|---|
Elasticsearch is a free, open, and distributed search and analytics engine for all types of data, including textual, numeric, geospatial, structured, and unstructured, with multi-tenancy capabilities, RESTful APIs and JSON-based search engine.
Elasticsearch is built on top of Apache Lucene and was first introduced in 2010 by Elasticsearch N.V. (now known as Elastic).
Elasticsearch is the core component of the Elastic Stack, a free and open set of tools for data ingestion, enrichment, storage, analysis, and visualization. Commonly referred to as the ELK Stack (for Elasticsearch, Logstash and Kibana)
# Kibana
 | Kibana (opens new window) |
|---|
Kibana is a data visualization and management tool for Elasticsearch that provides real-time histograms, line graphs, pie charts, and maps. Kibana also includes advanced applications such as Canvas, which allows users to create custom dynamic infographics based on their data, and Elastic Maps for visualizing geospatial data. It is a user interface that lets you visualize your Elasticsearch data and navigate the Elastic Stack.
With Kibana, you can:
Search, observe, and protect your data. From discovering documents to analyzing logs to finding security vulnerabilities, Kibana is your portal for accessing these capabilities and more.
Analyze your data. Search for hidden insights, visualize what you’ve found in charts, gauges, maps, graphs, and more, and combine them in a dashboard.
Manage, monitor, and secure the Elastic Stack. Manage your data, monitor the health of your Elastic Stack cluster, and control which users have access to which features.
# Logstash
| Logstash (opens new window) |
|---|
Logstash, one of the core products of the Elastic Stack, is used to aggregate and process data and send it to Elasticsearch. Logstash is an open source, server-side data processing pipeline that enables you to ingest data from multiple sources simultaneously and enrich and transform it before it is indexed into Elasticsearch.
Logstash can dynamically unify data from disparate sources and normalize the data into destinations of your choice. Cleanse and democratize all your data for diverse advanced downstream analytics and visualization use cases.
While Logstash originally drove innovation in log collection, its capabilities extend well beyond that use case. Any type of event can be enriched and transformed with a broad array of input, filter, and output plugins, with many native codecs further simplifying the ingestion process. Logstash accelerates your insights by harnessing a greater volume and variety of data.
# Filebeat
 | Filebeat (opens new window) |
|---|
Filebeat is a lightweight shipper for forwarding and centralizing log data. Installed as an agent on your servers, Filebeat monitors the log files or locations that you specify, collects log events, and forwards them either to Elasticsearch or Logstash for indexing. It is an Elastic Beat. It’s based on the libbeat framework.
When you start Filebeat, it starts one or more inputs that look in the locations you’ve specified for log data. For each log that Filebeat locates, Filebeat starts a harvester. Each harvester reads a single log for new content and sends the new log data to libbeat, which aggregates the events and sends the aggregated data to the output that you’ve configured for Filebeat.
# ISC DHCP
 | ISC DHCP (opens new window) |
|---|
Dynamic Host Configuration Protocol (DHCP) is a network protocol used to automatically assign IP addresses and basic settings to devices and computers on the local network that request them, reducing configuration time and facilitating administration. .
ISC DHCP offers a complete open source solution for implementing DHCP servers, relay agents and clients. ISC DHCP supports both IPv4 and IPv6, and is suitable for use in high-volume, high-reliability applications.
This plugin is integrated with FWCloud-UI. We can access the settings by displaying the System section.
In the next video you can see how to install, uninstall, configure and manage a DHCP server from the FWCloud-UI using this plugin:
# HAProxy
 | HAProxy (opens new window) |
|---|
HAProxy (High Availability Proxy) is a powerful, open-source software used for load balancing and proxying TCP and HTTP-based applications. It distributes incoming traffic across multiple backend servers to enhance the performance and provide high availability of websites and applications. HAProxy is commonly used to improve server load distribution, manage high traffic and provide redundancy in case of server failures.
In the next video we can see an example of how to install, configure and uninstall HAProxy from FWCloud-UI:
